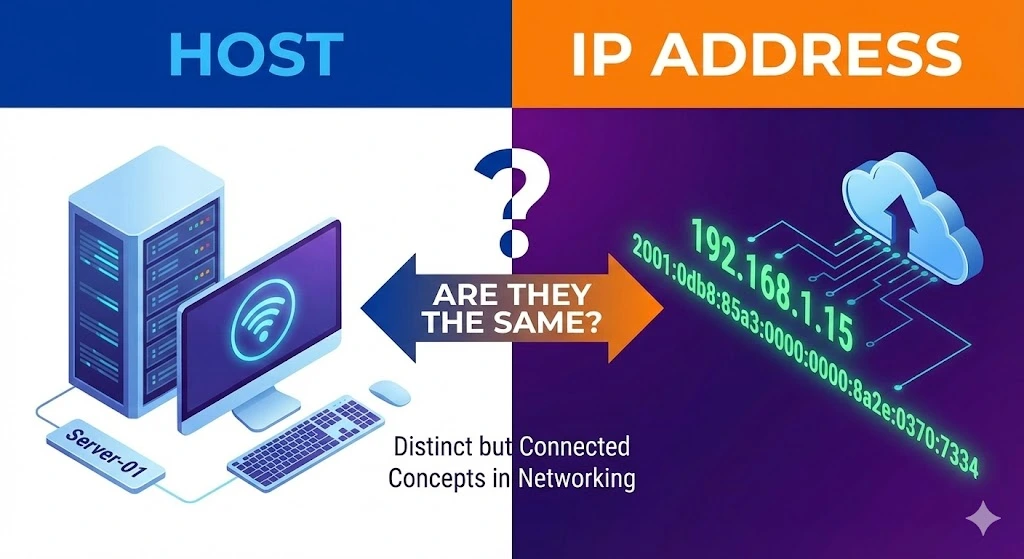
Are Host and IP Addresses the same?
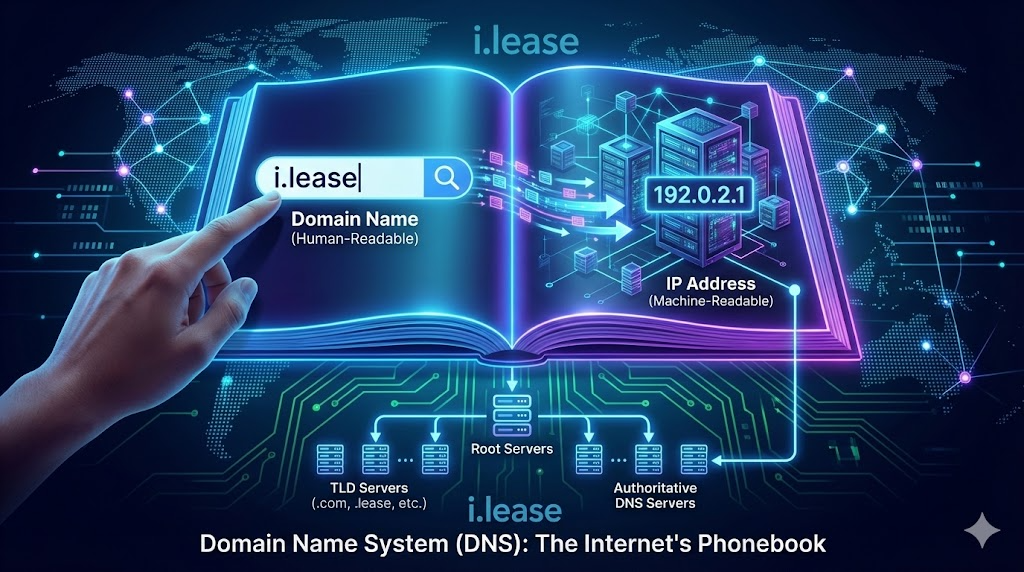
When learning the complexities of networking, you might encounter terms like “host” and “IP address” used frequently. These terms are fundamental to how devices communicate over the internet. While they are related, host and IP addresses are not the same. This article aims to clarify the differences and relationships between a host and an IP address, providing a comprehensive understanding of each term and their roles in network communication.Read more Related Posts What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more Top considerations when trading IPv4 addresses on the secondary market Navigating the IPv4 secondary market requires careful attention to legality, reputation, pricing, compliance and risk management to ensure successful transactions.Legal Read more IPv4 address price history from exhaustion to 2026 An exploration of IPv4 address price trends from scarcity‑driven spikes to market corrections, and how exhaustion shaped prices up to Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }