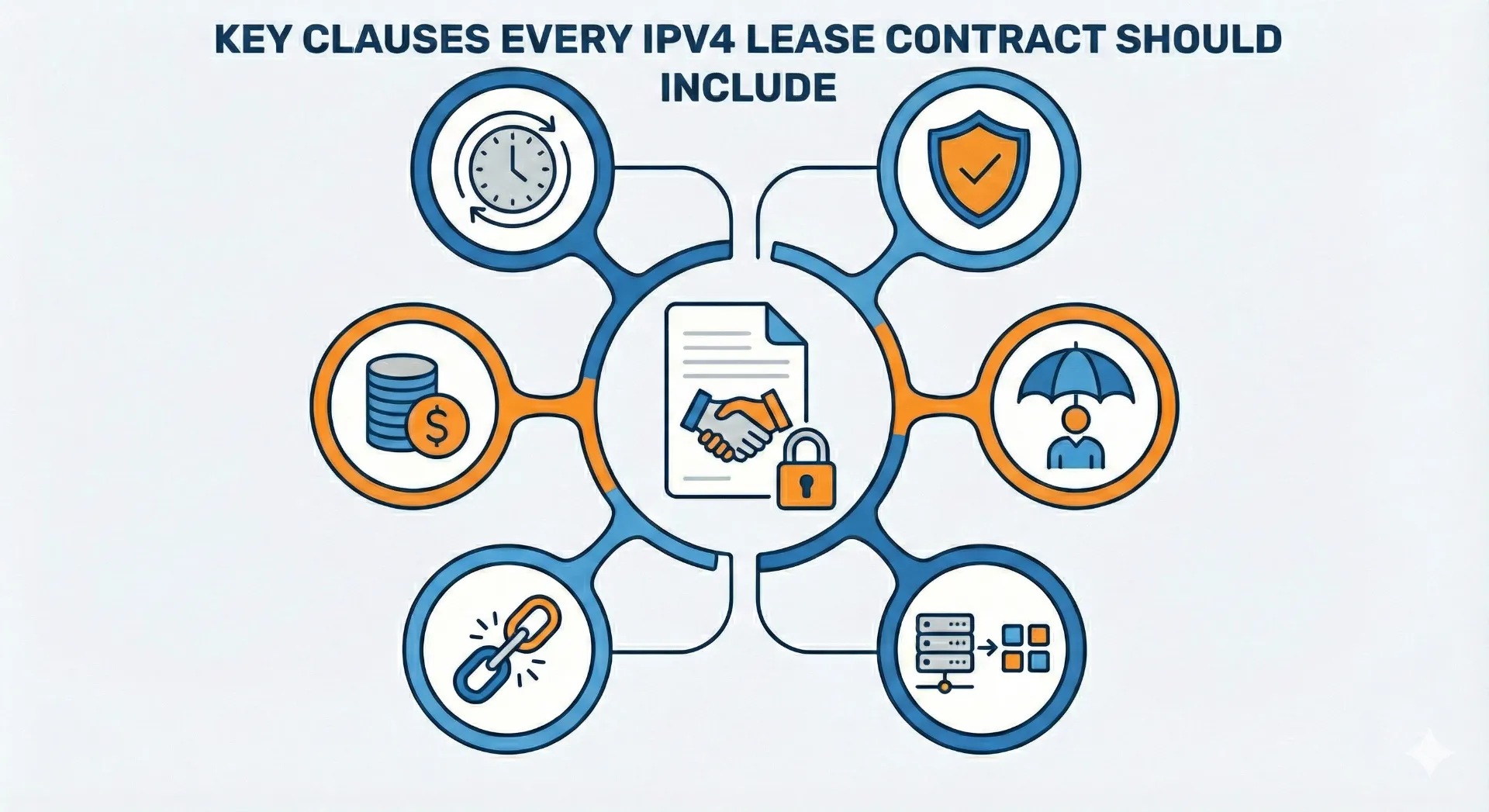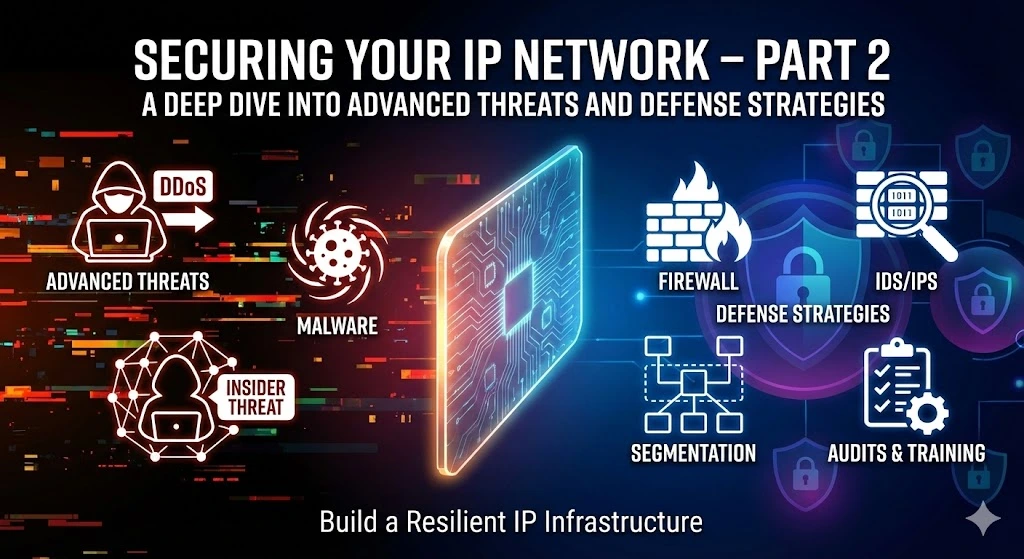
In Part 1 of our series, we explored the importance of securing your IP network and outlined fundamental strategies for enhancing network security. In this instalment, we will delve deeper into the specific measures and best practices for securing your IP addresses and safeguarding your network against cyber threats and unauthorized access. In this article, we will guide you through 6 methods of securing your IP network. ReferRead more