IP Reputation vs. IP Risk Score: What’s the Difference

A clear comprehension of the discrepancies between IP reputation and IP risk score constitutes a critical prerequisite for effective cybersecurity governance — the former encapsulates historical trustworthiness, while the latter forecasts potential threat vulnerabilities.
Table of Contents
Key Points
- IP reputation embodies the historical trustworthiness and past behavioural patterns of an IP address, exerting a direct influence on email deliverability and network access permissions.
- IP risk score integrates a broader spectrum of threat indicators and behavioural metrics to quantify the probability of malicious activity, with applications in fraud prevention, intrusion detection, and dynamic security screening protocols.
What is IP Reputation?
IP reputation can be formally defined as a quantitative and qualitative assessment of an IP address’s “trustworthiness” predicated on its historical behavioural patterns and operational track record.
This concept operates analogously to a credit scoring mechanism: an IP address with an unblemished history — characterized by the absence of spam dissemination, malware distribution, or abuse reports — attains a positive reputation. Conversely, involvement in suspicious or malicious activities such as spam propagation, phishing campaigns, or malware dissemination results in a degradation of reputation.
For instance, numerous email service providers, network security systems, and firewall solutions leverage IP reputation as a core criterion for filtering incoming traffic or email communications: IP addresses with compromised reputations may be subjected to blocking, quarantining, or flagging.
Owing to its focus on historical performance, IP reputation tends to exhibit relative stability (albeit with the potential for temporal changes). Adherence to cybersecurity hygiene practices — including the avoidance of spam, compliance with email sending best practices, and the prevention of abusive behaviours — is instrumental in sustaining a favourable reputation.
What is IP Risk Score?
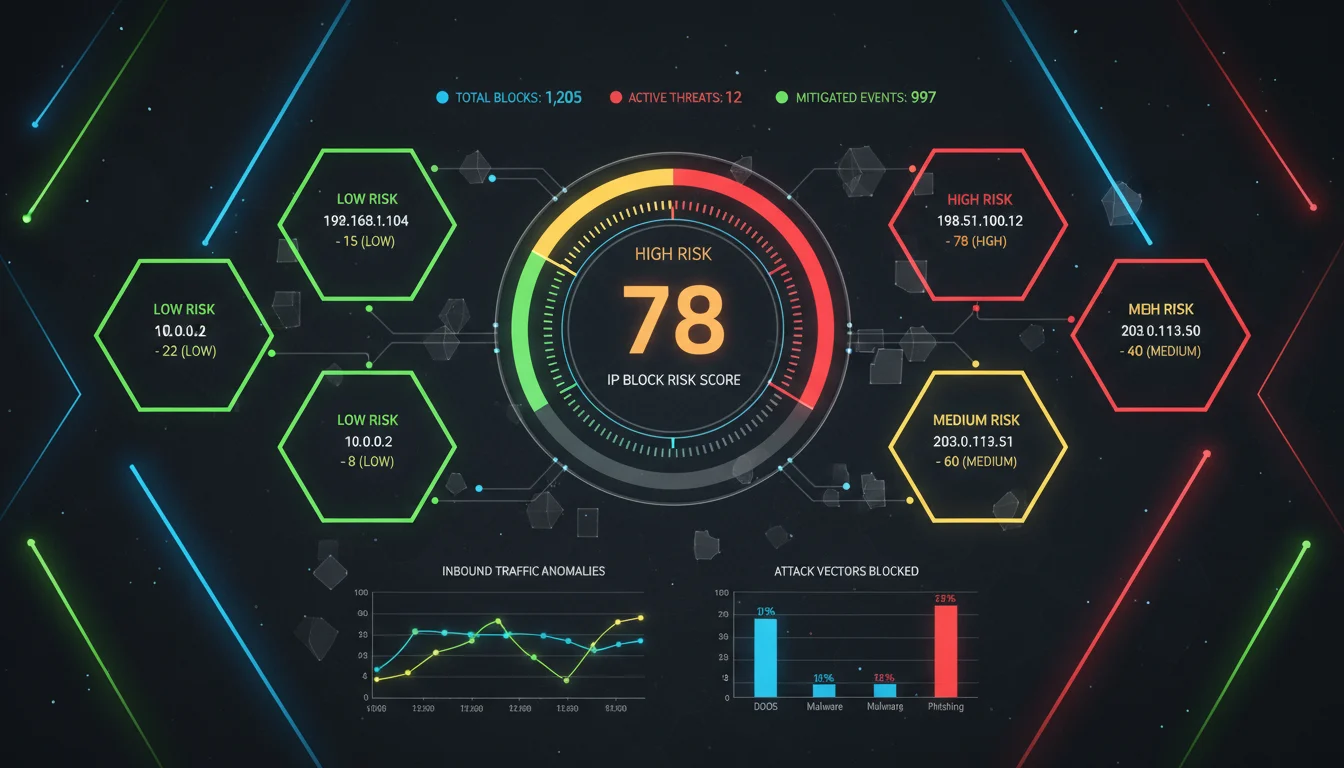
An IP risk score — alternatively termed an IP risk rating or IP fraud score — represents a dynamic and comprehensive evaluative framework designed to estimate the likelihood that an IP address is currently engaged in, or will imminently undertake, malicious activity, fraudulent behaviour, or other unwanted operational conduct.
In contrast to the retrospective focus of IP reputation, IP risk scoring systems aggregate a multifaceted set of variables: geolocation data, associations with proxy servers or virtual private networks (VPNs), entries in known blacklists, anomalous behavioural patterns (e.g., abrupt traffic surges, unauthorized login attempts, port scanning activities), and IP usage classification (e.g., residential IP, data-centre IP).
These scores are typically presented within predefined numerical ranges — for example, certain service providers employ scales of 0–100 or analogous gradients — wherein higher scores correspond to elevated risk levels or an increased probability of malicious intent.
IP risk scores are extensively deployed in real-time security contexts: e-commerce platforms utilize them to detect fraudulent transactions, financial institutions employ them for screening suspicious login attempts or monetary operations, online services leverage them to block bot or proxy traffic, and network security personnel utilize them to trigger enhanced scrutiny or proactive blocking measures.
Why the Distinction Matters
While IP reputation and IP risk score share conceptual overlaps, conflating these two constructs can lead to erroneous security judgments and suboptimal decision-making.
- Static vs. Dynamic Perspectives: IP reputation offers a retrospective analytical lens, documenting the historical actions of an IP address. In contrast, IP risk score provides a predictive or contextual assessment, forecasting potential future behaviours based on real-time signals and environmental factors.
- Divergent Use Cases: Reputation metrics are predominantly utilized for long-term trust evaluation, such as email deliverability optimization or the establishment of general network allow-lists. Risk scores, by contrast, are applied in real-time scenarios, including fraud detection, context-sensitive access control, and behavioural anomaly identification.
- Granularity and Nuance: Risk scoring frameworks incorporate transient behavioural indicators (e.g., sudden login attempts, proxy utilization) and environmental contextual data (e.g., geolocation, internet service provider type), dimensions that may not be fully captured by reputation-based assessments alone.
For organizations engaged in the development of secure systems — encompassing email servers, online platforms, and security-critical services — the synergistic application of both metrics can significantly enhance the reliability and robustness of security architectures.
How IP Reputation is Calculated: Typical Signals
IP reputation assessment services derive their evaluations from a diverse array of data sources:
- Historical email transmission patterns, spam or abuse complaint records, and entries in blacklist databases.
- Evidence of prior malicious activities, including malware distribution, botnet participation, and phishing campaigns.
- Email authentication verification and compliance adherence (for email-sending IPs): validation of proper Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) configurations, as well as maintenance of low bounce rates and complaint ratios.
Given its reliance on historical and aggregated data, the classification resulting from IP reputation analysis tends to be stable, with changes typically triggered by the occurrence of new negative events.
How IP Risk Score is Calculated: More Dynamic Signals
Risk scoring systems incorporate a broader and more dynamically updated set of evaluative criteria, including:
- Geolocation anomalies (e.g., IP addresses originating from high-risk regions, frequent geographic location shifts, or utilization of VPN/proxy services).
- IP type and internet service provider (ISP) classification: differentiation between data-centre, hosting provider, residential ISP, or proxy network-assigned IPs, with data-centre and proxy IPs often associated with elevated risk profiles.
- Behavioural patterns: irregular login frequencies, rapid sequential requests, port scanning activities, brute-force attack attempts, or other indicators of automated or bot-driven behaviour.
- Blacklist status: presence in known abuse repositories, spam/malware blacklists, or records of prior fraud or attack-related activities.
- Contextual data: integration with device fingerprinting information, session history, user-agent identifiers, or other metadata. Within fraud-prevention workflows, IP risk metrics may be combined with behavioural, transactional, or identity-related signals to enhance predictive accuracy.
As a consequence of this multifaceted data integration, IP risk scores can undergo rapid fluctuations: an IP address previously classified as “clean” based on reputation may be flagged as high-risk if it exhibits suspicious usage patterns, and vice versa.
IP-based indicators are noisy and prone to false positives, so they should be used cautiously as only one component of a broader risk-assessment strategy
-Sarabi, Karir & Liu, “Scoring the Unscorables: Cyber Risk Assessment Beyond Internet Scans.
Use Cases: When to Rely on Reputation, When on Risk Score
Email and Deliverability Systems
Organizations operating email service providers, marketing platforms, or transactional email services frequently rely on IP reputation to determine the routing of incoming mail or to filter unwanted content. A positive reputation is critical for ensuring message delivery to recipient inboxes, while a compromised reputation may result in blocking, quarantining, or deliverability impairments.
Real-Time Security and Fraud Prevention
Platforms facilitating user logins, financial transactions, or access to sensitive data commonly employ IP risk scores as integral components of fraud detection or intrusion prevention systems. Suspicious IP addresses may be flagged for additional verification, subjected to access restrictions, or blocked outright.
Zero-Trust and Adaptive Security Architectures
Within zero-trust security frameworks — which operate on the principle of “never trust, always verify” — every connection, login attempt, or data access request is subject to dynamic evaluation. In this context, IP reputation serves as a baseline trust indicator, while IP risk scores (reflecting real-time contextual data) trigger adaptive security controls in response to detected high-risk signals.
External Attack Surface and Threat-Intelligence Monitoring
Organizations engaged in monitoring their external digital attack surfaces utilize reputation data to maintain “clean” IP address pools, while simultaneously applying risk scoring methodologies to preempt emerging threats or vulnerabilities.
Why Using Both Matters: Layered Security and Trust
Exclusive reliance on IP reputation can create security vulnerabilities: an IP address with a positive historical record may be compromised at a later stage, rendering reputation-based assessments obsolete. Conversely, overreliance on IP risk scores may result in the over-flagging of benign IP addresses, leading to unnecessary disruptions.
By integrating both metrics — historical trustworthiness (reputation) and real-time risk context (risk score) — organizations can implement a nuanced, layered security approach:
- Leverage reputation metrics for long-term allow-list configurations, baseline trust evaluations, and email deliverability decisions.
- Utilize risk scores for real-time decision-making processes, including adaptive security protocols (e.g., login risk assessment, fraud detection, content filtering).
This hybrid strategy achieves a balance between operational reliability and security resilience, enabling organizations to trust legitimate actors while maintaining vigilance against emerging threats.
IP risk scoring is now a core defence layer in an era where threats hide inside trusted infrastructures
—Alex Morgan, Cybersecurity Strategist
Challenges and Limitations
Data Quality and Coverage
Reputation databases are contingent upon the accuracy and timeliness of historical activity records. For IP addresses with insufficient monitoring (e.g., newly allocated IPs, dynamically assigned addresses, shared IP pools), reputation assessments may be incomplete or misleading.
Risk scoring systems depend on the integration of multiple data sources and heuristic algorithms, which inherently introduce the potential for false positives and false negatives — particularly in edge cases involving legitimate users utilizing VPNs or proxy services.
Dynamic IP Allocation and Shared Hosting Environments
Modern cloud hosting, shared hosting, and VPN services frequently reuse IP addresses across multiple clients. This practice means that an IP address classified as “clean” at one point may subsequently be utilized for malicious purposes, thereby compromising both reputation and risk assessments.
Transparency and Interpretability
IP risk scores are often generated by proprietary algorithms incorporating numerous variables, making it challenging for organizations to interpret the specific factors contributing to a given IP’s classification. This lack of transparency can hinder the implementation of targeted corrective actions.
Over-Blocking and Business Impact
Excessive reliance on risk scores may result in the blocking or challenging of legitimate users, negatively impacting user experience — particularly among privacy-conscious individuals, VPN users, or legitimate users accessing services via proxy servers.
Expert Perspective
Security analysts emphasize that “IP reputation serves as a foundational component of modern spam and threat filtering mechanisms, providing a framework for identifying trustworthy IP addresses.”
Concurrently, within zero-trust security environments, “reputation alone is insufficient to govern access decisions — real-time risk signals must be integrated to enable dynamic security responses.”
Industry practitioners consistently advocate that “robust cybersecurity requires a layered approach to metrics, combining historical reputation data with real-time risk scoring to adapt to the evolving threat landscape.”
Best Practices for Organisations
Dual Monitoring of Reputation and Risk
Avoid treating IP reputation and IP risk score as interchangeable metrics; each fulfills distinct functions within security and deliverability infrastructure.
Prioritize Risk Scoring for High-Sensitivity Events
Deploy IP risk scores for critical operations such as user logins, financial transactions, registration processes, and access to sensitive data.
Leverage Reputation for Baseline Trust and Long-Term Decisions
Utilize IP reputation for email sending optimization, general firewall whitelisting, and the management of low-risk traffic flows.
Regular Re-evaluation of IP Pools
Conduct periodic assessments of IP address pools — especially those associated with shared hosting or cloud services — to identify reputation degradation or sudden risk spikes.
Integrate IP Signals with Multifactor Authentication Combine IP-based metrics with device fingerprinting, behavioural monitoring, and user authentication protocols to enhance overall security posture.
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
Get Started with i.leaseFrequently Asked Questions
Q1: Can an IP Address Possess a Good Reputation but a High Risk Score?
Yes. An IP address may maintain a clean historical record (positive reputation) while exhibiting current risky behaviours or operating within a high-risk environment (e.g., VPN usage, shared data-centre infrastructure), resulting in a elevated risk score.
Q2: Is IP Risk Score More Effective Than IP Reputation for Fraud Prevention?
Generally, yes. IP risk scores incorporate dynamic environmental factors (e.g., proxy utilization, geolocation anomalies, suspicious activity patterns) beyond the scope of historical reputation, rendering them more suitable for fraud detection and real-time security decision-making.
Q3: Can an IP Address’s Reputation Improve Over Time?
Yes. An IP address previously associated with abusive behaviours can gradually restore its reputation if it maintains a sustained period of compliant operation — characterized by the absence of spam, malicious activity, or abuse reports — as recognized by reputation assessment services.
Q4: Are There Standardized Ranges for IP Risk Scores, or Are They Vendor-Specific?
IP risk score ranges are predominantly vendor-specific. Different service providers employ varying scales (e.g., 0–100, 0–10, or custom risk categorizations) based on their proprietary algorithms and data models.
Q5: Should Organisations Rely Exclusively on One Metric (Reputation or Risk Score)?
No. Best practice mandates the combined utilization of both metrics: reputation for baseline trust evaluation and long-term reliability assessments, and risk score for dynamic, context-aware security and fraud prevention.
Related Blogs
Related Posts

Common Myths About Selling IP Addresses
The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they fear the perceived complexity or legal “gray areas.” As IPv4 exhaustion becomes a permanent reality, the value of these addresses has skyrocketed, yet misconceptions continue to stall potential transactions. At i.lease, powered by the real-world expertise of LARUS, we’ve seen how these myths prevent companies from unlocking significant capital.Read more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to buy IPv4 addresses through a certified IP broker
Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global transfers. IPv4 transactions are regulated transfers, not simple purchases — registries must approve documentation, justification and registration changes. Certified brokers reduce risk and delay by aligning buyers with registry policy, routing legitimacy and cross-region requirements. Why companies still need to buy IPv4 addresses The global supply of IPv4 addressesRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to turn idle IPv4 addresses into a recurring revenue stream with iLease
Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while navigating market demand, compliance and risk. Leasing idle IPv4 blocks can generate steady, long-term income without relinquishing ownership. Platforms like i.lease global IPv4 marketplace make it easier to monetise addresses and manage reputation and compliance. why IPv4 addresses still matter Despite the long-anticipated exhaustion of the IPv4 address space — aRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }