Understanding the Different Types of DDoS Attacks

Table of Contents
As the internet becomes more integral to everyday business operations, cybersecurity threats evolve in both complexity and impact. One of the most persistent and damaging threats facing organizations today is the Distributed Denial of Service (DDoS) attack. These attacks flood a targeted system with an overwhelming amount of traffic, rendering services unusable for legitimate users.
To effectively mitigate DDoS threats, it’s essential to understand the various types of attacks cybercriminals deploy. Each type targets a specific layer of the network or system infrastructure, and knowing how each one operates is the first step toward building a resilient defense strategy.
In this post, we’ll explore the main types of DDoS attacks, breaking them down into their categories and detailing how they disrupt services.
1. Volume-Based Attacks
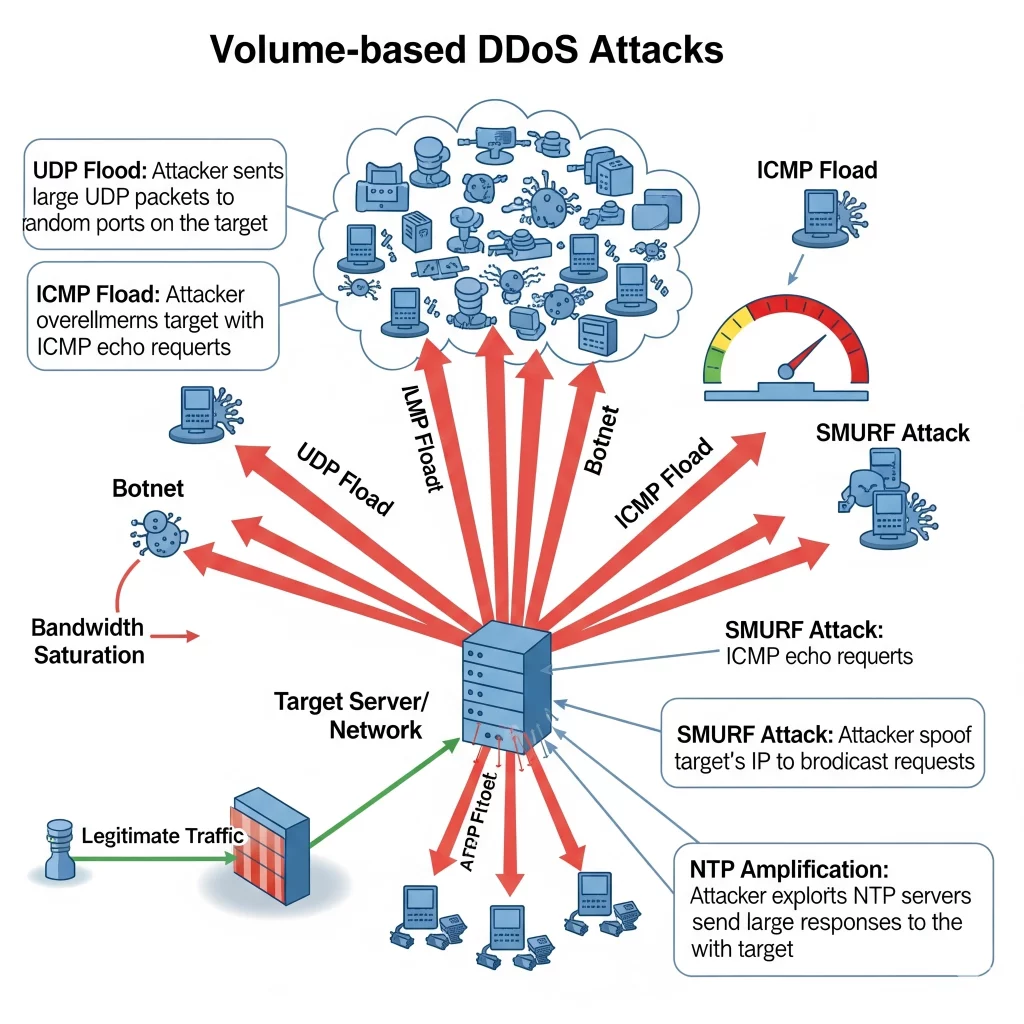
Volume-based DDoS attacks aim to saturate the bandwidth of the target site. They are the most common type and often involve botnets sending massive amounts of traffic.
Key Examples:
- UDP Flood: A large number of UDP packets are sent to random ports on the target machine, forcing it to respond continuously.
- ICMP Flood: This uses ICMP echo requests (pings) to flood the target, consuming both outgoing and incoming bandwidth.
- DNS Amplification: Attackers spoof the victim’s IP and send DNS queries to open DNS resolvers, which respond with large amounts of data, amplifying the traffic hitting the target.
Impact:
These attacks are designed to consume all available bandwidth, effectively taking the target offline by exhausting its capacity.
2. Protocol Attacks
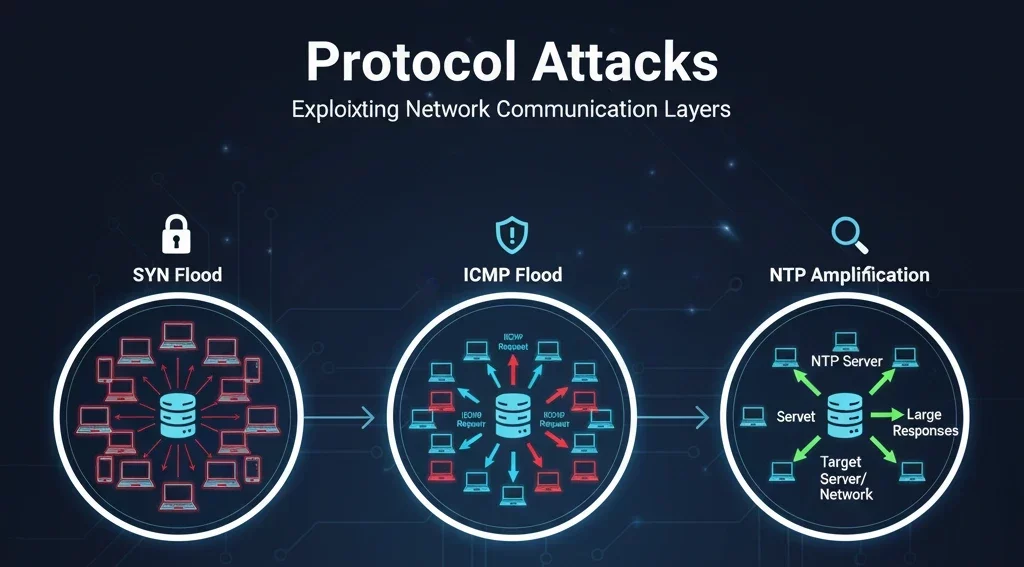
Protocol attacks exploit weaknesses in network layer protocols. These attacks target servers and intermediate resources like firewalls and load balancers.
Key Examples:
- SYN Flood: Exploits the TCP handshake process by sending repeated SYN requests with spoofed IP addresses, never completing the connection.
- Ping of Death: Sends maliciously crafted ping packets that exceed the maximum allowed size, causing systems to crash or reboot.
- Smurf Attack: An attacker sends ICMP requests with a spoofed source address (the victim) to a network’s broadcast address, causing a flood of responses.
Impact:
These attacks consume server resources, and because they target the infrastructure itself, they can be harder to detect and mitigate.
3. Application Layer Attacks
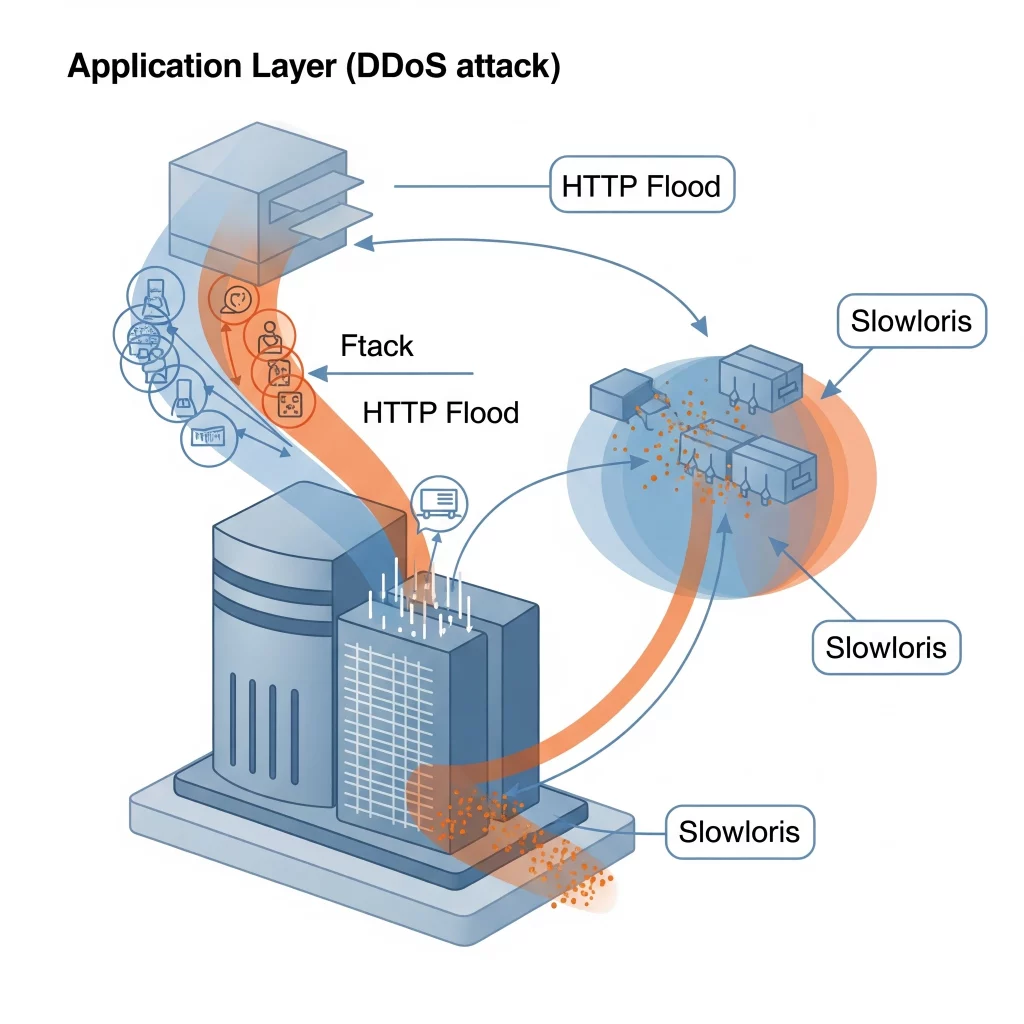
Application layer (Layer 7) attacks mimic legitimate user behavior, making them difficult to distinguish from normal traffic. They target the actual applications, such as web servers.
Key Examples:
- HTTP Flood: Attackers send seemingly legitimate HTTP requests, overwhelming the web server’s capacity to process requests.
- Slowloris: Keeps many connections to the target web server open and holds them open as long as possible by sending partial HTTP requests.
- Zero-day Exploits: These attacks exploit unknown or unpatched vulnerabilities in applications to cause crashes or service interruptions.
Impact:
These attacks are highly stealthy and resource-intensive, aiming to exhaust application resources rather than network bandwidth.
4. Multi-Vector Attacks
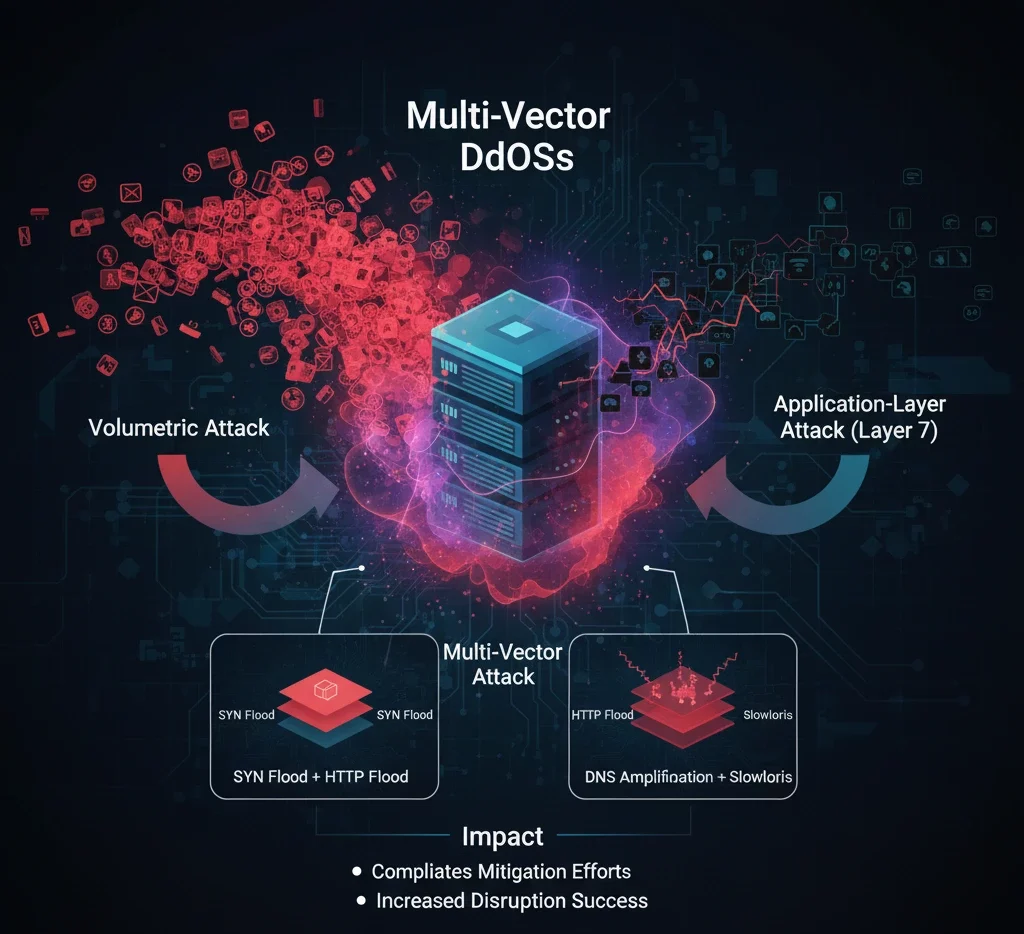
Multi-vector attacks combine two or more different types of DDoS strategies. For example, an attacker might initiate a volumetric attack while simultaneously targeting the application layer.
Key Examples:
- Combining SYN floods with HTTP floods.
- Using DNS amplification in conjunction with Slowloris.
Impact:
By mixing attack types, these methods complicate mitigation efforts and increase the chance of successful disruption.
Why It Matters
Understanding these DDoS variations is critical for implementing a comprehensive defense. Organizations must deploy layered security solutions, conduct regular vulnerability assessments, and ensure that both infrastructure and applications are equipped to detect and mitigate DDoS activity.
In addition to traditional firewalls and intrusion prevention systems, DDoS protection services and real-time traffic monitoring tools play vital roles in identifying and mitigating threats before they escalate.
Final Thoughts
DDoS attacks are becoming more sophisticated, but with a deep understanding of how each type functions, businesses can stay one step ahead. A well-informed security posture, complemented by robust mitigation strategies, is essential for safeguarding your digital presence.
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
Get Started with i.leaseRelated Blogs
Related Posts

Common Myths About Selling IP Addresses
The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they fear the perceived complexity or legal “gray areas.” As IPv4 exhaustion becomes a permanent reality, the value of these addresses has skyrocketed, yet misconceptions continue to stall potential transactions. At i.lease, powered by the real-world expertise of LARUS, we’ve seen how these myths prevent companies from unlocking significant capital.Read more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to buy IPv4 addresses through a certified IP broker
Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global transfers. IPv4 transactions are regulated transfers, not simple purchases — registries must approve documentation, justification and registration changes. Certified brokers reduce risk and delay by aligning buyers with registry policy, routing legitimacy and cross-region requirements. Why companies still need to buy IPv4 addresses The global supply of IPv4 addressesRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to turn idle IPv4 addresses into a recurring revenue stream with iLease
Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while navigating market demand, compliance and risk. Leasing idle IPv4 blocks can generate steady, long-term income without relinquishing ownership. Platforms like i.lease global IPv4 marketplace make it easier to monetise addresses and manage reputation and compliance. why IPv4 addresses still matter Despite the long-anticipated exhaustion of the IPv4 address space — aRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }