In today’s digital landscape, businesses and organizations rely heavily on seamless connectivity and secure access to online resources. However, IP blocking has become a common challenge, often disrupting operations, limiting access to critical platforms, and even affecting business continuity. One innovative solution to this problem is Bring Your Own IP (BYOIP), a strategy that allows organizations to retain control over their IP addresses and mitigate the risks associated withRead more
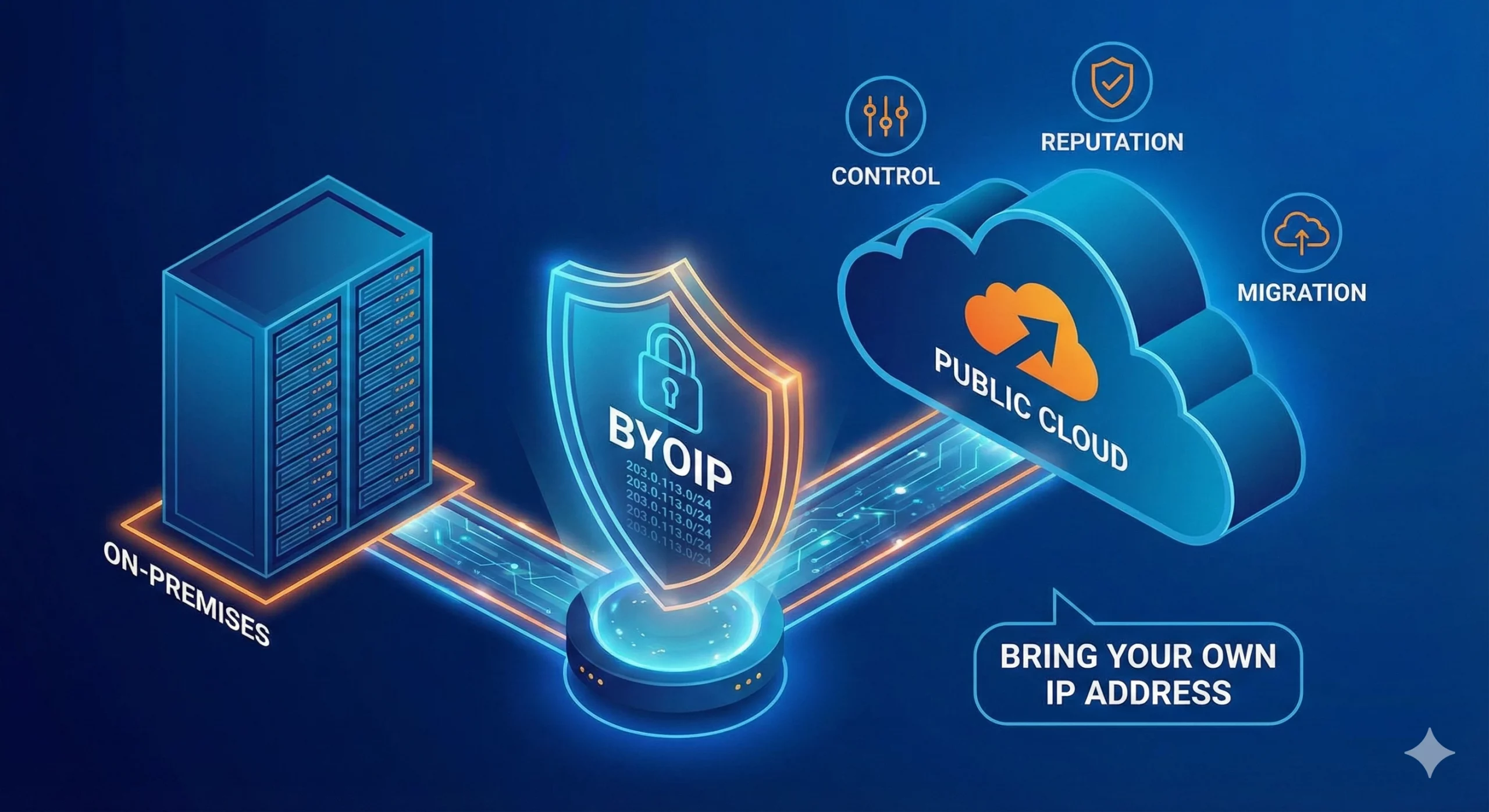
Bring Your Own IP (BYOIP) is a concept in cloud computing and networking that allows businesses to bring and use their own Internet Protocol (IP) address ranges when migrating to cloud service providers (CSPs) or other networking infrastructures. This approach enables organizations to maintain their existing IP addresses instead of adopting new ones assigned by the provider, ensuring consistency, security, and operational continuity. Why is BYOIP Important? Organizations thatRead more

Elastic IP addresses (EIPs) are a crucial component of cloud networking, especially in Amazon Web Services (AWS). They provide a static, public IPv4 address that can be associated with an instance, ensuring reliability even if the instance is stopped and restarted. However, improper management of Elastic IPs can lead to security risks, unnecessary costs, and operational inefficiencies. This blog post outlines the best practices for effectively managing Elastic IPRead more
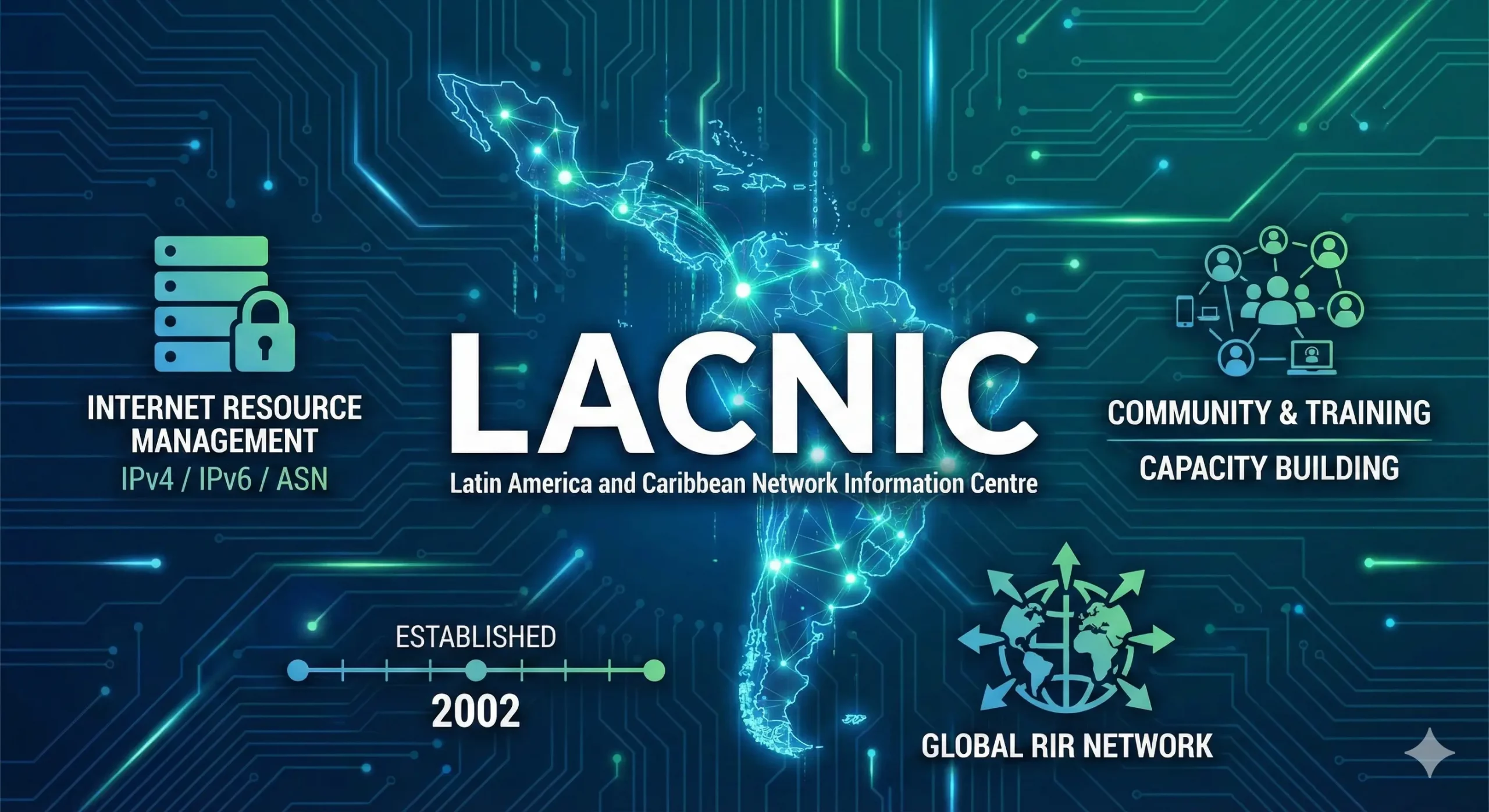
LACNIC: Strengthening Internet Infrastructure in Latin America and the Caribbean The Latin America and Caribbean Network Information Center (LACNIC) plays a vital role in shaping the digital landscape of Latin America and the Caribbean. As the region’s designated Regional Internet Registry (RIR), LACNIC is responsible for managing and distributing Internet number resources, including IPv4, IPv6 addresses, and Autonomous System Numbers (ASNs). Operating as a non-profit community-led organization, LACNIC ensuresRead more
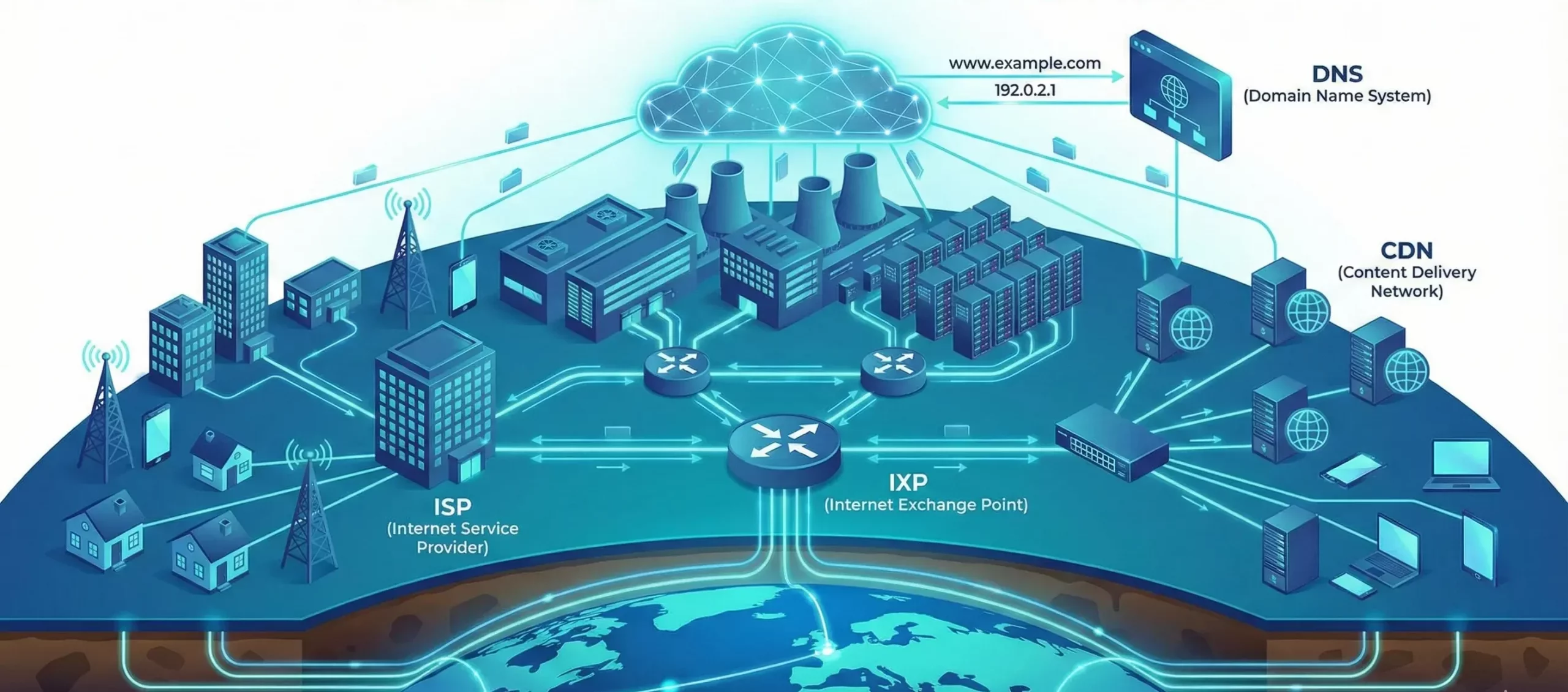
The Internet is essential to modern life, connecting billions of people and devices worldwide. But have you ever wondered what makes it work? The Internet relies on a complex infrastructure of physical and digital components that work together seamlessly. Let’s dive into the key elements that power the global web. Physical Internet Infrastructure: The Internet’s Highway The Internet relies on physical hardware to transmit data across the globe. TheseRead more