The Potential Risks of Using Public IP Addresses (Part 1)

Public IP addresses allow devices to communicate directly with the internet, but they also come with several risks that can jeopardize security and privacy. This article explores the potential dangers associated with using public IP addresses and offers tips on how to mitigate these risks in Part 2
Table of Contents
What is a public IP address?
A public IP address is an address that is accessible over the internet. It is assigned by an Internet Service Provider (ISP) and can be used by any device connected to the Internet to communicate with other devices. Unlike private IP addresses, which are used within a local network and are not accessible from outside, public IP addresses are visible to everyone on the internet.
Potential Risks of Public IP Addresses
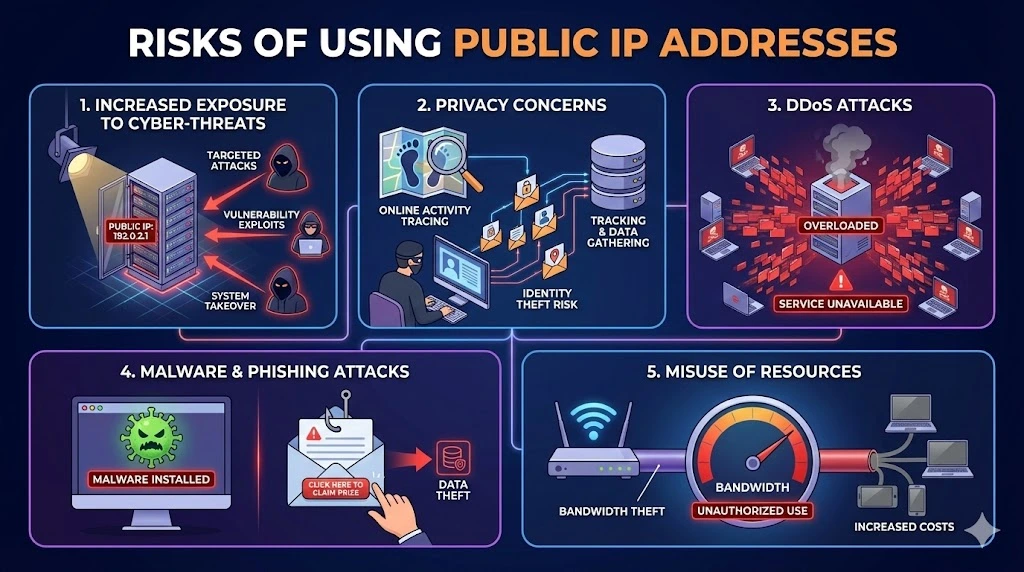
Increased Exposure to Cyber-threats
One of the primary risks of using public IP addresses is increased exposure to cyber threats. Since public IP addresses are accessible over the internet, they can be targeted by hackers who use various methods to exploit vulnerabilities. This can lead to unauthorized access to sensitive information, data breaches, and even complete system takeovers.
Privacy Concerns
Public IP addresses can be tracked and monitored, leading to significant privacy concerns. Malicious actors can use public IP addresses to trace online activities, gather personal information, and even pinpoint physical locations. This information can be used for identity theft, stalking, or other malicious purposes.
Distributed Denial of Service (DDoS) Attacks
Public IP addresses are often the target of distributed denial of service (DDoS) attacks. In a DDoS attack, multiple compromised systems flood a target system with traffic, overwhelming it and causing it to become unavailable. These attacks can disrupt business operations, cause financial losses, and damage reputations.
Malware and Phishing Attacks
Devices with public IP addresses are more susceptible to malware and phishing attacks. Hackers can exploit vulnerabilities to install malware on a device, which can then be used to steal data, monitor activities, or launch further attacks. Phishing attacks, where attackers trick individuals into providing sensitive information, are more likely when public IP addresses are involved.
Misuse of Resources
When using public IP addresses, there is a risk that unauthorized users can misuse your network resources. This can include bandwidth theft, where others use your internet connection without permission, leading to slower internet speeds and increased costs.
Summary of The Article
While public IP addresses are necessary for certain internet functionalities, they come with inherent risks. By understanding these risks and implementing appropriate security measures, individuals and organizations can protect themselves from potential threats and ensure their online activities remain secure.
Discover the potential risks of using public IP addresses and learn how to protect your network from cyber attacks, privacy breaches, and other threats. Taking proactive steps to safeguard public IP addresses is essential in today’s digital landscape. Stay tuned for part 2!
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
Get Started with i.leaseFAQs
Can someone find my exact location from my Public IP address?
Not your exact street address. A Public IP address typically reveals your approximate location (Country, City, and ISP). However, legal authorities can subpoena your ISP to reveal your exact physical address and identity if illegal activity is suspected.
Is it safer to use a Static or Dynamic Public IP address?
A Dynamic IP (which changes periodically) is generally considered slightly safer for home users because it makes it harder for hackers to target you consistently over time. Static IPs are easier to target but are often necessary for businesses hosting servers or CCTV systems.
Can I change my Public IP address to stop an attack?
Yes. If you have a Dynamic IP, simply unplugging your modem/router for 5-10 minutes (or sometimes overnight) is often enough to get assigned a new IP address by your ISP. If you have a Static IP, you must contact your ISP and request a change due to security concerns.
Related Posts

Common Myths About Selling IP Addresses
The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they fear the perceived complexity or legal “gray areas.” As IPv4 exhaustion becomes a permanent reality, the value of these addresses has skyrocketed, yet misconceptions continue to stall potential transactions. At i.lease, powered by the real-world expertise of LARUS, we’ve seen how these myths prevent companies from unlocking significant capital.Read more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to buy IPv4 addresses through a certified IP broker
Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global transfers. IPv4 transactions are regulated transfers, not simple purchases — registries must approve documentation, justification and registration changes. Certified brokers reduce risk and delay by aligning buyers with registry policy, routing legitimacy and cross-region requirements. Why companies still need to buy IPv4 addresses The global supply of IPv4 addressesRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to turn idle IPv4 addresses into a recurring revenue stream with iLease
Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while navigating market demand, compliance and risk. Leasing idle IPv4 blocks can generate steady, long-term income without relinquishing ownership. Platforms like i.lease global IPv4 marketplace make it easier to monetise addresses and manage reputation and compliance. why IPv4 addresses still matter Despite the long-anticipated exhaustion of the IPv4 address space — aRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }