Blog

Internet Censorship and the Great Firewall: Understanding the Boundaries of the Digital World The Internet has revolutionized the way we connect, learn, and share information, but its open nature has also led to significant debates about control, privacy, and freedom. Table of Contents Toggle Internet Censorship and the Great Firewall:
Go ahead
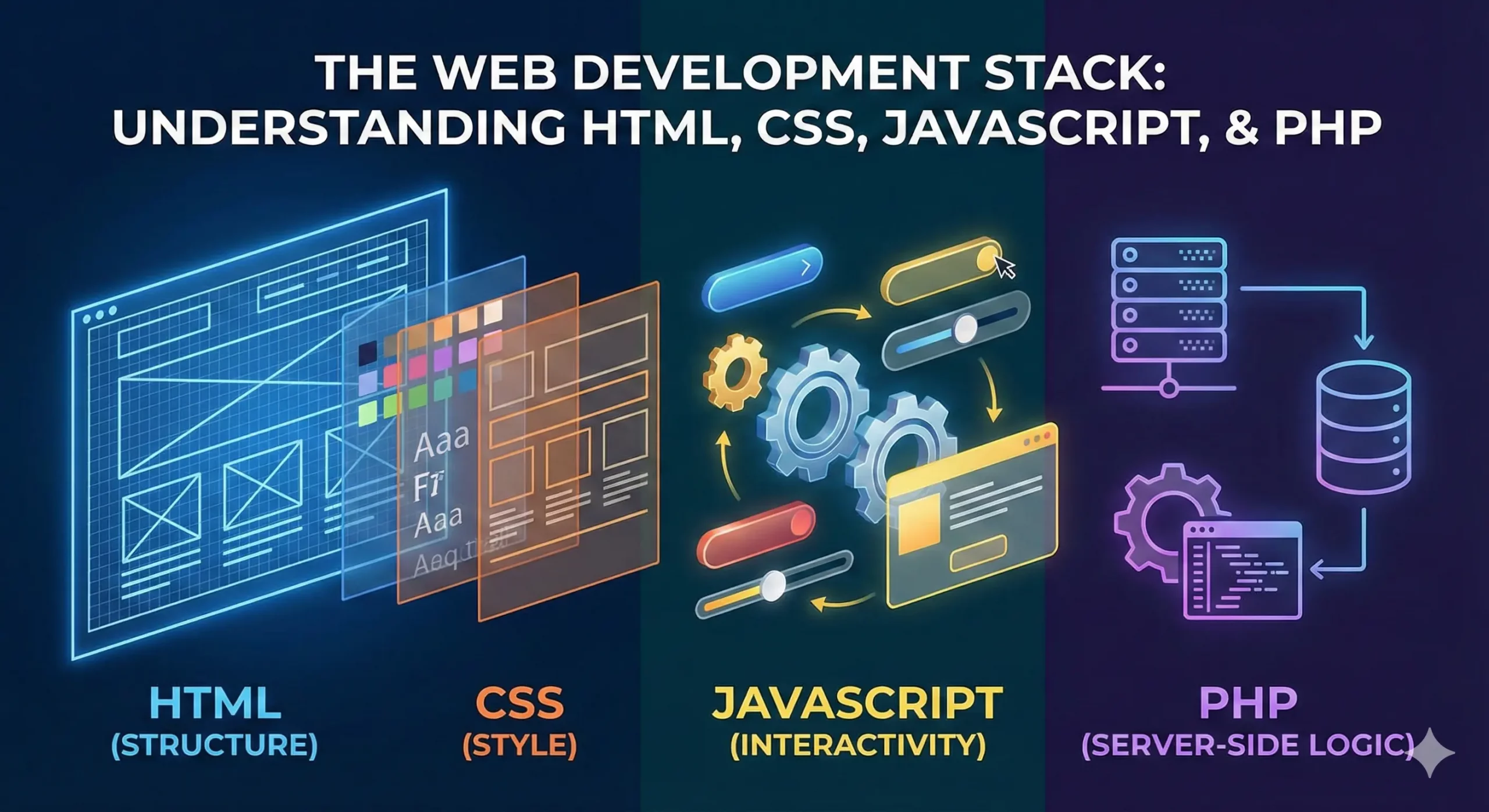
The world of web development may sound intimidating, but understanding its foundational languages—HTML, CSS, JavaScript, and PHP—can simplify it for anyone. These languages play distinct roles in creating the websites and applications you interact with daily. Here’s a breakdown: Table of Contents Toggle HTML (HyperText Markup Language)CSS (Cascading Style Sheets)JavaScriptPHP
Go ahead

29November
What is GeoIP and How Does It Work?
GeoIP is crucial in tailoring online experiences, improving cybersecurity, and powering countless business applications. But what exactly is GeoIP, how does it work, and why is it so important? Let’s dive in. Table of Contents Toggle What is GeoIP?How Does GeoIP Work?1. IP Address Lookup2. Mapping Data3. Location Identification4. Application
Go ahead
25November
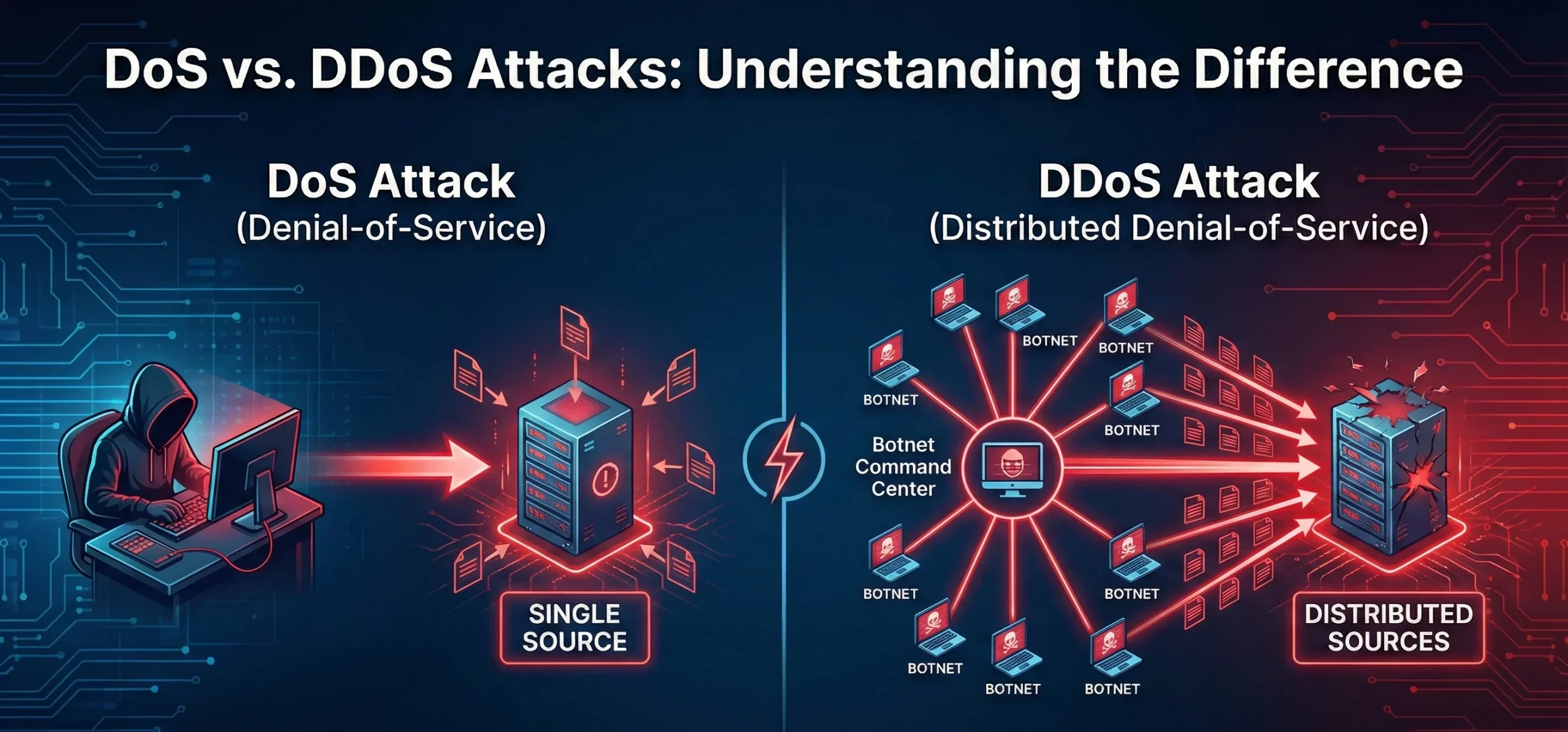
Difference between DOS and DDOS attacks
What Are DoS and DDoS Attacks? A Denial of Service (DoS) attack attempts to make a machine, network, or service unavailable to users by overwhelming traffic or requests. It typically originates from a single source. Table of Contents Toggle What Are DoS and DDoS Attacks?Key Characteristics of DoS & DDoS
Go ahead
Understanding ICANN: The Internet's Governing Body Table of Contents Toggle Understanding ICANN: The Internet's Governing BodyICANN’s Role in Domain Names and IP AddressesImpact on Global Internet GovernanceHow ICANN Impacts Users and the Future of the InternetWhy ICANN MattersTrusted IPv4 Leasing for Business Growth The Internet Corporation for Assigned Names and
Go ahead
