Mitigating the Risks of Public IP Addresses (Part 2)

While the risks associated with public IP addresses are significant, several measures can be taken to mitigate these dangers. Here’s a detailed guide on how to protect your network from the potential hazards of using public IP addresses.
Table of Contents
Use Firewalls
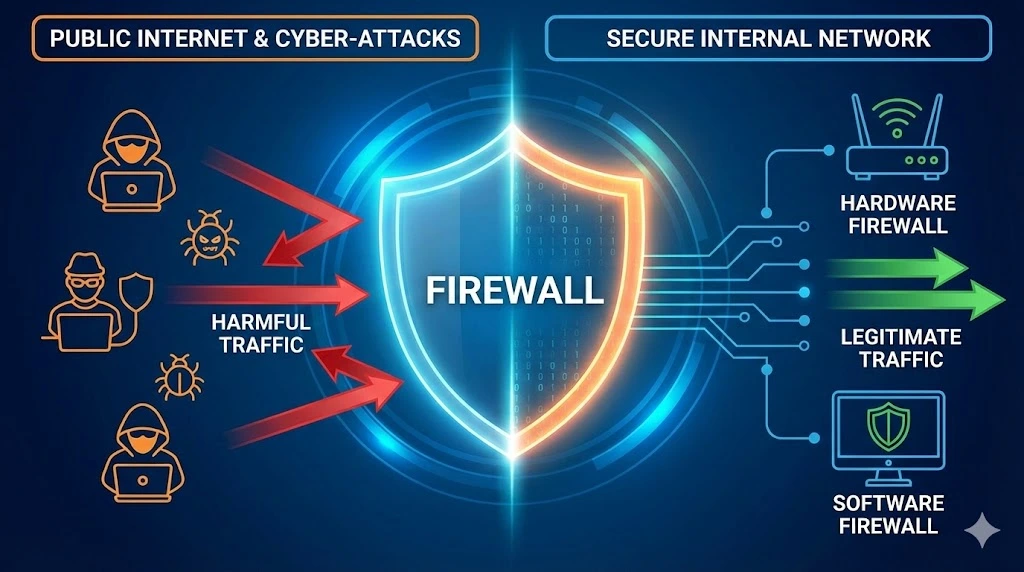
Implementing a robust firewall is one of the first lines of defense against unauthorized access and cyber-attacks. Firewalls act as a barrier between your internal network and the internet, filtering traffic and blocking potentially harmful connections. By monitoring incoming and outgoing traffic based on predefined security rules, firewalls help ensure that only legitimate traffic is allowed through.
Firewalls can be hardware-based, software-based, or a combination of both. For most users, a combination of a hardware firewall provided by their router and a software firewall on their computer or server offers a comprehensive security solution.
Enable Network Address Translation (NAT)
Network Address Translation (NAT) is an essential feature for enhancing security when using public IP addresses. NAT allows multiple devices on a local network to share a single public IP address. This process adds a layer of security by masking the internal IP addresses from an external view, making it more difficult for attackers to target specific devices within your network.
NAT works by translating the private IP addresses of devices within the network into a single public IP address when communicating with external networks. This translation process helps to keep internal network details hidden from potential attackers.
Regular Software Updates
Keeping all software, including operating systems and applications, up to date is crucial for maintaining network security. Software updates often include patches for security vulnerabilities that hackers could exploit. Regularly updating software reduces the risk of these vulnerabilities being used to gain unauthorized access to your network.
Automated update systems can help ensure that your software remains current. For critical systems and applications to apply updates as soon as they become available.
Implement Strong Passwords and Authentication

Using strong passwords and multi-factor authentication (MFA) can significantly reduce the risk of unauthorized access. Strong passwords should be complex, containing a mix of letters, numbers, and special characters. Avoid using easily guessable information such as birthdays or common words.
Multi-factor authentication adds an extra layer of security by requiring additional verification steps beyond just the password. This could include a fingerprint scan, a one-time code sent to a mobile device, or other verification methods. Enabling MFA wherever possible enhances security by making it more challenging for attackers to gain access to accounts and devices.
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
Get Started with i.leaseFAQs
Can someone hack me with just my Public IP address?
Not directly. Knowing your IP address is like knowing your home address—it tells people where you are, but it doesn’t give them a key to the front door.
Does a Dynamic IP address protect me better than a Static IP?
Slightly, yes. A Dynamic IP changes periodically (assigned by your ISP), making it harder for hackers to target you over a long period. A Static IP remains the same, making it a consistent target for Distributed Denial of Service (DDoS) attacks if not properly protected.
Is Public Wi-Fi dangerous for my IP address?
Yes. Public Wi-Fi networks (like in cafes) often lack encryption. Hackers on the same network can potentially intercept your data or perform “Man-in-the-Middle” attacks. Always use a VPN or disable “File Sharing” when connecting to public hotspots to mitigate this risk.
Related Posts

Common Myths About Selling IP Addresses
The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they fear the perceived complexity or legal “gray areas.” As IPv4 exhaustion becomes a permanent reality, the value of these addresses has skyrocketed, yet misconceptions continue to stall potential transactions. At i.lease, powered by the real-world expertise of LARUS, we’ve seen how these myths prevent companies from unlocking significant capital.Read more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to buy IPv4 addresses through a certified IP broker
Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global transfers. IPv4 transactions are regulated transfers, not simple purchases — registries must approve documentation, justification and registration changes. Certified brokers reduce risk and delay by aligning buyers with registry policy, routing legitimacy and cross-region requirements. Why companies still need to buy IPv4 addresses The global supply of IPv4 addressesRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to turn idle IPv4 addresses into a recurring revenue stream with iLease
Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while navigating market demand, compliance and risk. Leasing idle IPv4 blocks can generate steady, long-term income without relinquishing ownership. Platforms like i.lease global IPv4 marketplace make it easier to monetise addresses and manage reputation and compliance. why IPv4 addresses still matter Despite the long-anticipated exhaustion of the IPv4 address space — aRead more Related Posts Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to buy IPv4 addresses through a certified IP broker Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global Read more What happens when IP resources are mismanaged Poor IP resource management can lead to outages, security breaches, blacklisting, legal exposure and reputational damage across networks and business Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }