Securing communications between devices is important, especially when managing remote systems. One of the most widely used and trusted protocols for secure remote access is SSH (Secure Shell). This article will dive into what SSH is, how it works, and why it’s so important for network security. What is SSH? SSH (Secure Shell) is a network protocol that allows users to access and manage remote computers securely over anRead more
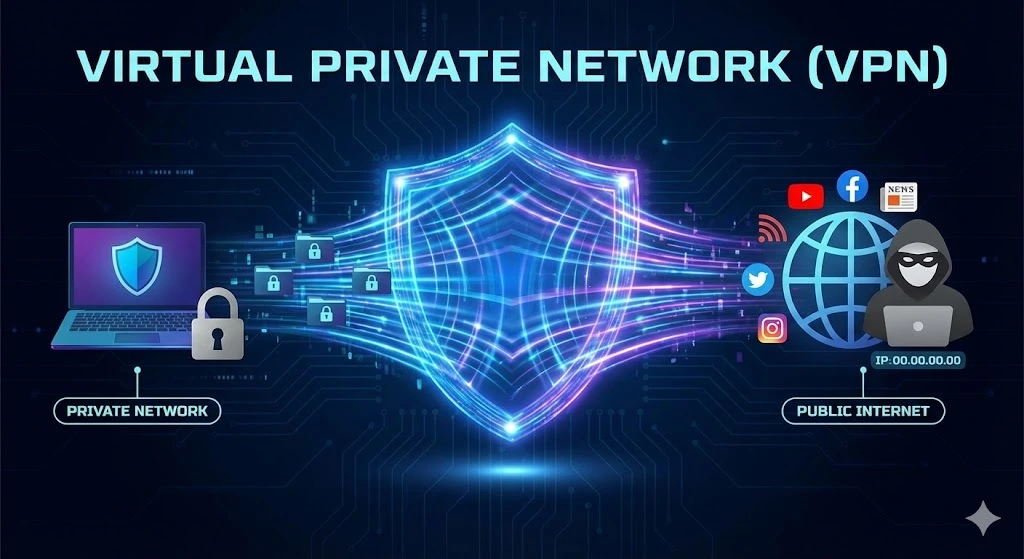
What is a VPN? A Virtual Private Network (VPN) is a technology that allows users to create a secure connection to another network over the Internet. By encrypting your data, a VPN hides your online activities, making it harder for hackers, advertisers, or even your ISP to track your browsing behavior. Essentially, a VPN acts as a tunnel, shielding your Internet traffic from prying eyes and ensuring privacy andRead more

Internet fraud refers to the use of the Internet to deceive individuals or organizations for personal or financial gain. With the rise of e-commerce, online banking, and digital communication, internet fraud has become a global issue. It encompasses a wide range of deceptive practices, from identity theft and phishing scams to online auction fraud and credit card fraud. Criminals exploit the anonymity of the internet to trick unsuspecting users,Read more
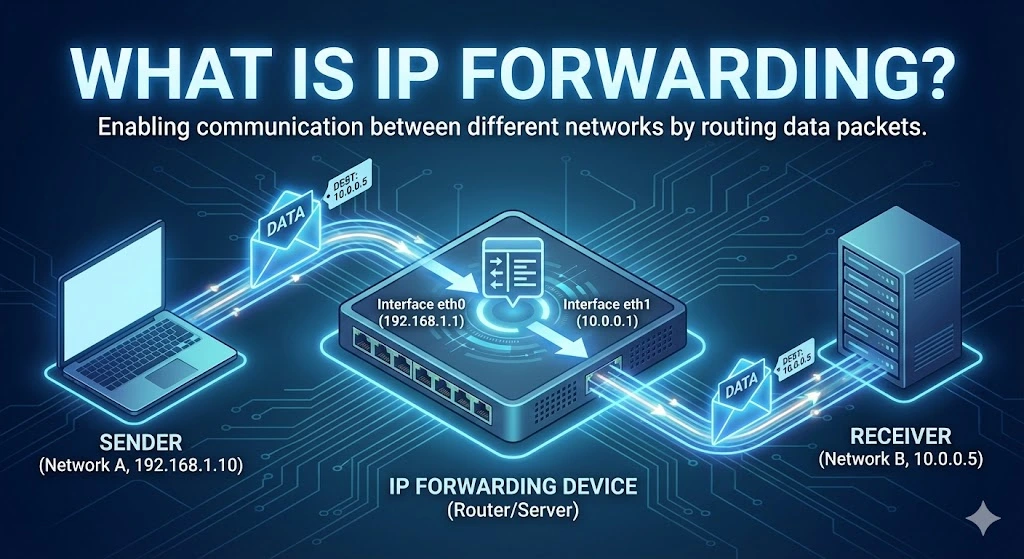
IP forwarding is the process by which a network device, such as a router, forwards or relays IP (Internet Protocol) packets from one network to another. It enables communication between different network segments by directing data packets to their appropriate destination IP addresses. When a device forwards packets that are not destined for its IP address, it acts as a gateway, passing data from one network to another, typicallyRead more
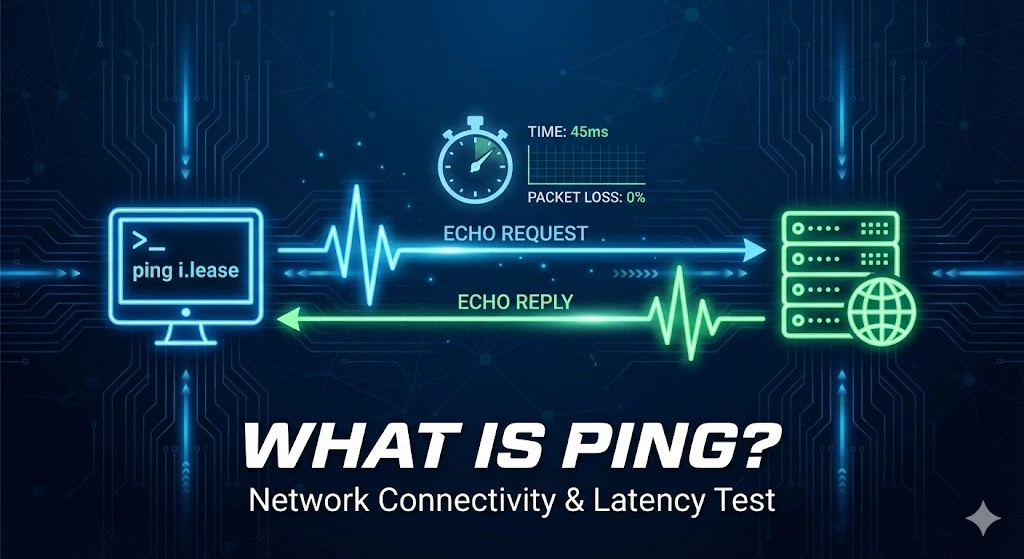
Ping is a network diagnostic tool used to test the connection between your device and another on a network, typically the Internet. It is named after the sound made by sonar in submarines, where a signal is sent out, and the echo is awaited. In networking terms, it sends out packets of data to a specific IP address and waits for a response, telling you if the destination isRead more