How Law Enforcement Tracks Hackers and Telco Scammers: Tools & Techniques
Cybercrime is on the rise, with hackers and telco scammers using sophisticated methods to hide their identities. Law enforcement agencies rely on advanced IP tracking tools, forensic analysis, and cyber intelligence to trace and catch these criminals. In this article, we’ll explore the top tools and techniques used by authorities worldwide to track down cybercriminals.
Table of Contents
ToggleIP Tracking & Geolocation Tools
To pinpoint the location of a hacker, authorities use IP tracking and geolocation tools such as MaxMind GeoIP, IPinfo.io, and Whois Lookup. These tools provide insights into an IP address’s physical location, associated ISP, and network details. Shodan and Censys further help by scanning connected devices to reveal potential vulnerabilities that hackers might exploit.
Network Traffic Analysis & Packet Capture
Monitoring real-time network traffic is essential in cybercrime investigations. Tools like Wireshark, Tcpdump, and Zeek (Bro IDS) allow law enforcement to capture and analyze network packets, helping to identify malicious activity. These tools can detect unauthorized connections, suspicious data transfers, and unusual traffic spikes that may indicate cybercrime activities.
Digital Forensics & Log Analysis
Cybercriminals often leave digital footprints that can be uncovered through forensic analysis. Tools like Autopsy, X-Ways Forensics, and Splunk help authorities analyze logs, recover deleted files, and trace an attacker’s movements. ELK Stack (Elasticsearch, Logstash, Kibana) and Graylog provide powerful log monitoring capabilities, assisting in tracking hacker activities over time.
OSINT (Open-Source Intelligence) Tools
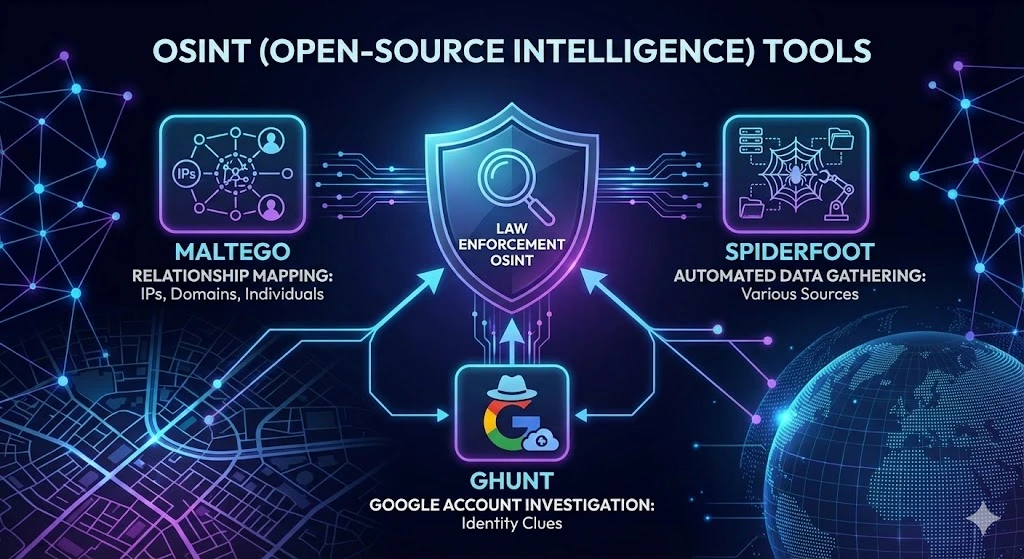
Law enforcement leverages OSINT tools to collect intelligence from publicly available sources. Maltego helps map relationships between IPs, domains, and individuals, while SpiderFoot automates data gathering from various sources. Additionally, GHunt can investigate Google account activity, providing valuable clues about a suspect’s identity.
Tor & Dark Web Monitoring
Hackers and scammers frequently use Tor and dark web platforms to operate anonymously. Tools like Ahmia and OnionScan assist in uncovering hidden services, while CipherTrace and Chainalysis track cryptocurrency transactions linked to cybercrime. Law enforcement also employs ShadowDragon to monitor darknet activities and uncover criminal networks.
ISP Collaboration & Legal Requests
One of the most effective ways to trace hackers is through ISP collaboration. Law enforcement agencies issue subpoenas and MLAT (Mutual Legal Assistance Treaty) requests to obtain user logs from ISPs. Programs like LEAP (Law Enforcement Access Program) and organizations such as Interpol, FBI, and Europol work together to track cybercriminals across borders.
Anti-VPN & Proxy Detection
Many hackers use VPNs, proxies, or the Tor network to mask their real IP addresses. Tools like IPQualityScore, FraudLabs Pro, and Scamalytics help detect these disguises by identifying suspicious IP patterns, VPN usage, and proxy servers. These solutions help law enforcement unmask hidden attackers.
Honeypots & Cyber Threat Intelligence
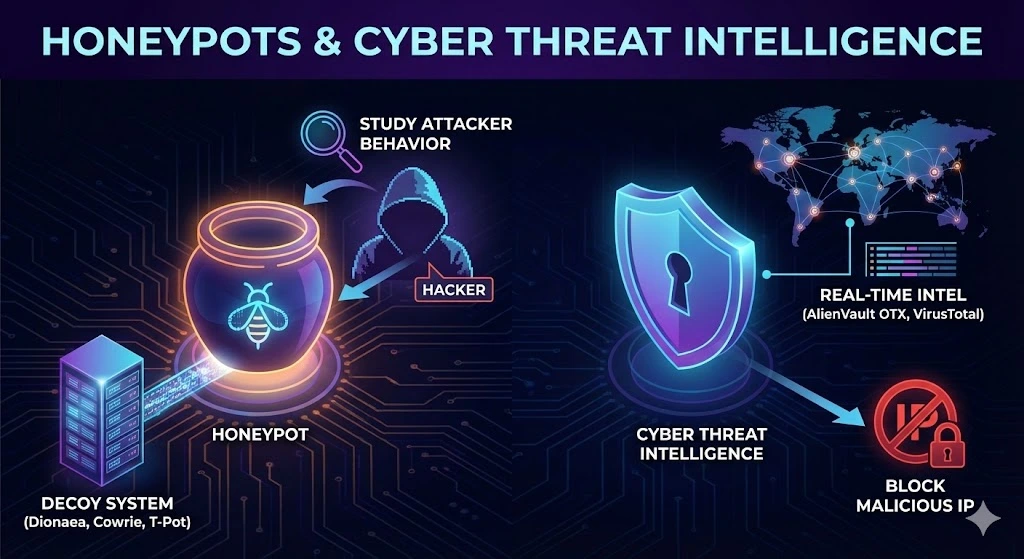
To catch cybercriminals, law enforcement deploys honeypots—decoy systems designed to lure hackers. Tools like Dionaea, Cowrie, and T-Pot simulate vulnerable systems, allowing authorities to study attacker behavior. Additionally, AlienVault OTX and VirusTotal provide real-time threat intelligence, helping to identify and block malicious IP addresses.
Advanced & Government-Level Tracking
Top intelligence agencies employ advanced surveillance programs to track cybercriminals worldwide. XKeyscore (NSA tool) and PRISM (U.S. surveillance program) collect vast amounts of internet data. Echelon, a global surveillance system, monitors communications for national security threats. Meanwhile, Palantir Gotham integrates AI-powered analytics for large-scale investigations.
How Law Enforcement Tracks Hackers & Scammers
To successfully track and apprehend cybercriminals, law enforcement follows a multi-layered approach. This includes IP geolocation tracking, ISP subpoenas, network traffic analysis, OSINT research, and social engineering tactics. Some agencies conduct undercover dark web operations to infiltrate hacking forums and identify criminal masterminds. By combining cutting-edge technology with intelligence collaboration, authorities can track and prosecute hackers effectively.
Final Thoughts
As cyber threats continue to evolve, so do the tools and techniques used by law enforcement to track and locate hackers and scammers. By leveraging IP tracking, digital forensics, OSINT, honeypots, and dark web monitoring, authorities can uncover cybercriminal networks and bring them to justice. If you’re in cybersecurity, law enforcement, or digital forensics, staying ahead of these trends is critical to combating online threats.
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
A clear comprehension of the discrepancies between IP reputation and IP risk score constitutes a critical prerequisite for effective cybersecurity Read more
Organisations increasingly rely on IP risk scores. They use them to assess threat levels. They reduce fraud losses. They strengthen Read more
The current era faces IPv4 address scarcity. Organizations must verify IP block risk scores. Tools like i.lease help complete this Read more



