Securing Your IP Network: Part 1

In this tech-driven world, keeping your IP network safe is like locking the doors to your digital house. It’s crucial for protecting your important stuff, keeping things running smoothly, and dodging online troublemakers. As businesses rely more on networks for everything from chats to storing files, beefing up security is vital. So, let’s dive into some simple ways to keep your IP network locked down and fend off those cybercriminals.
Table of Contents
Why do we need to secure the IP network?
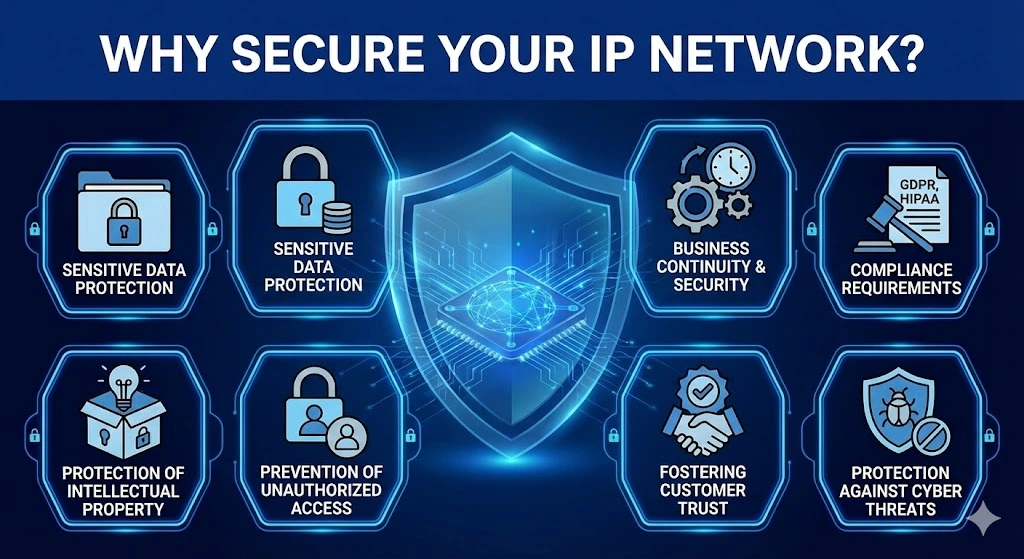
Securing an IP network is essential for most businesses. Here are the reasons:
Protection of Sensitive Data
IP networks often transmit sensitive information, such as personal data, financial records, and intellectual property. Securing the network helps prevent unauthorized access and data breaches, safeguarding sensitive information from theft or misuse.
Business Continuity & Security
A secure IP network ensures uninterrupted operations by mitigating the risk of cyber attacks, system compromises, and network outages. By implementing robust security measures, businesses can maintain continuity and prevent disruptions to critical services and operations.
Compliance Requirements
Many industries are subject to regulatory requirements and compliance standards governing data security and privacy. Securing the IP network helps organizations comply with regulatory mandates such as GDPR, HIPAA, PCI DSS, and others, avoiding penalties, legal liabilities, and reputational damage.
Protection Against Cyber Threats
The Internet is rife with cyber threats such as malware, ransomware, phishing attacks, and DDoS (Distributed Denial of Service) attacks. Securing the IP network helps defend against these threats, reducing the risk of data loss, financial losses, and reputational harm.
Fostering Customer Trust
Maintaining a secure IP network builds trust and confidence among customers, partners, and stakeholders. By demonstrating a commitment to cybersecurity, businesses can reassure customers that their data is protected and their privacy is respected, enhancing customer loyalty and brand reputation.
Prevention of Unauthorized Access
Securing the IP network prevents unauthorized users from gaining access to network resources, systems, and data. Access controls, encryption, and authentication mechanisms help verify the identity of users and restrict access to authorized personnel only, reducing the risk of insider threats and unauthorized activities.
Protection of Intellectual Property
Intellectual property (IP) assets such as proprietary software, trade secrets, and confidential business information are valuable assets that require protection. Securing the IP network helps safeguard intellectual property from theft, espionage, and unauthorized disclosure, preserving competitive advantage and innovation.
Securing IP Address in a brief
Overall, securing an IP network is essential for protecting sensitive data, ensuring business continuity, complying with regulatory requirements, defending against cyber threats, building trust with customers, preventing unauthorized access, and safeguarding intellectual property. Investing in robust security measures helps organizations mitigate risks, strengthen their cybersecurity posture, and maintain a resilient and trustworthy network infrastructure.
Stay tuned for Part 2, where we’ll dive deeper into foolproof tips to secure your IP network! Don’t miss out!
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
Get Started with i.leaseFAQs
What are the most common vulnerabilities in an IP network?
The most common vulnerabilities include unpatched software, weak administrative passwords, open ports (like RDP or Telnet), and lack of encryption for data in transit. Regularly performing vulnerability scans and maintaining a strict update schedule are the first steps to closing these digital “doors.”
How does a secure IP network help with GDPR and HIPAA compliance?
These regulations mandate that personal and health data must be protected against unauthorized access. A secure network uses Encryption (TLS/SSL) and Access Control Lists (ACLs) to ensure that only authorized personnel can access sensitive information, directly fulfilling the “Security of Processing” requirements of these laws.
Can a secure IP network prevent DDoS attacks?
While a standard firewall can stop some small attacks, modern DDoS (Distributed Denial of Service) attacks require specialized mitigation tools. These tools detect unusual traffic spikes and “scrub” the traffic to ensure only legitimate users reach your network, maintaining your business continuity even during an attack.
Related Posts

Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises
Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key points Distinguishes between inbound (leasing in) and outbound (leasing out) IPv4 approaches and their strategic implications. Highlights contract structures, registry risk management and continuity considerations affecting global number resources. Inbound vs. outbound IPv4 leasing: complete enterprise guide In the post-exhaustion era of Internet Protocol version 4 (IPv4),Read more Related Posts Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key Read more Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to turn idle IPv4 addresses into a recurring revenue stream with iLease Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

Common Myths About Selling IP Addresses
The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they fear the perceived complexity or legal “gray areas.” As IPv4 exhaustion becomes a permanent reality, the value of these addresses has skyrocketed, yet misconceptions continue to stall potential transactions. At i.lease, powered by the real-world expertise of LARUS, we’ve seen how these myths prevent companies from unlocking significant capital.Read more Related Posts Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key Read more Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to turn idle IPv4 addresses into a recurring revenue stream with iLease Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to buy IPv4 addresses through a certified IP broker
Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global transfers. IPv4 transactions are regulated transfers, not simple purchases — registries must approve documentation, justification and registration changes. Certified brokers reduce risk and delay by aligning buyers with registry policy, routing legitimacy and cross-region requirements. Why companies still need to buy IPv4 addresses The global supply of IPv4 addressesRead more Related Posts Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key Read more Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to turn idle IPv4 addresses into a recurring revenue stream with iLease Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }