IP Allocation Best Practices for Enterprises

Table of Contents
- An essential yet commonly disregarded, crucial component that influences network security and efficient operation is a well-designed IP allocation scheme.
- Scalable growth now calls for the implementation of methodologies like variable-length subnet masking (VLSM) and IPv6 integration planning.
Laying the groundwork with a logical hierarchy
IP address allocation is a more fundamental element that the typically occurs just like an afterthought in the grand architecture of an enterprise network, where debates frequently concentrate on cutting-edge firewalls, zero-trust models, and cloud migrations. The process is historical, organic, as well as chaotic for numerous organizations. Whenever a new office opens, a subnet gets established, and a new project is assigned a random block. However, this ad-hoc approach may result in an intricate network that blocks scalability, creates security policies more challenging to put into effect, and leads to administrative nightmares.
Think about your IP address space as the foundation of your entire digital operation, rather than merely an assortment of numbers. Network engineers must approach IP allocation tactically, just as a city planner would not plan roads without a map. When executed correctly, a well-designed IP scheme is invisible, enabling seamless interaction, simplifying troubleshooting, and providing an established structure for security enforcement. A poorly designed one hinders down innovation and creates risk, becoming an ongoing source of problems. Tim Winters, a senior network architect at the University of New Hampshire InterOperability Laboratory (UNH-IOL), says:
“The biggest mistake we see is companies treating their internal IP address space as an unmanaged wasteland.”
— Tim Winters, University of New Hampshire InterOperability Laboratory (UNH-IOL)
An in-depth review is the initial stage towards successful IP address management. What you do not measure, you cannot under control. This involves documenting each IP subnet which is right now in use, alongside its size, operation, location, and rate of utilization. From fundamental command-line scripts to complicated commercial IP Address Management (IPAM) solutions, there are and are many tools accessible to assist with this discovery process. Inefficiencies could be identified through this starting inventory, such as the wastage of well over 240 addresses while a /24 subnet (254 addresses) gets assigned to a faraway branch office with just ten devices. Establishing a logical hierarchy is the next step shortly after you have a clear picture of where you are now. The strategic allocation of the intellectual property depends regarding this.
The primary goal is to establish an addressing scheme that is compatible with the company’s logical structure. Large companies tend to tailor their IP approach with either geography, business function, or both. For instance, you could figure out that the continent or country code is delimited by the second octet of your private 10.0.0.0/8 space. A specifics city or campus could be represented by the third octet. Individual devices would then be recognized by the fourth octet. This results in concerning right away clarity. An engineer might quickly identify that the device is situated at the main headquarters (12) in London (84) if they observe the address 10.84.12.45. Applying security policies and efficiently routing traffic is made achievable by this hierarchical model.
At this point in time, it’s practically difficult to reach an agreement on technical best practices like Variable-Length Subnet Masking (VLSM).Using the same subnet size everywhere was an accepted method in traditional subnetting, which is highly wasteful. With VLSM, it’s possible to precisely configure subnets of different dimensions by determining the number of hosts required within one’s larger network. A wireless access point might need a /30 subnet (2 addresses) for its point-to-point link, a server rack may need a /29 subnet (6 usable addresses) for its management interfaces, and a large office might need a /23 (510 addresses) for its user devices. All of these can be distributed from a single, perpetual address block with gaps along with inefficiencies thanks to VLSM. As available addresses grow more scarce, mastering VLSM could prove to be the most essential ability for maximizing your IPv4 address space.
The role of dhcp and static assignments
Within these well-designed subnets, the assignment of addresses to individual devices must also be managed carefully. The foundation of user devices that include laptops, phones, and tablets is the Dynamic Host Configuration Protocol (DHCP). It simplifies the process, prevents human error, and enables successful address reuse. Cependant not everything ought to have a dynamic. Establishing a particular range for static assignments within each subnet is the best obviously for action in this instance. In a /24 subnet, for example, you can set separate addresses.1 to.30 for servers and network infrastructure, while DHCP handles addresses.50 to.254. This defines a transparent and consistent pattern that every one of the team’s scientists will understand.
The importance of documentation in ip management
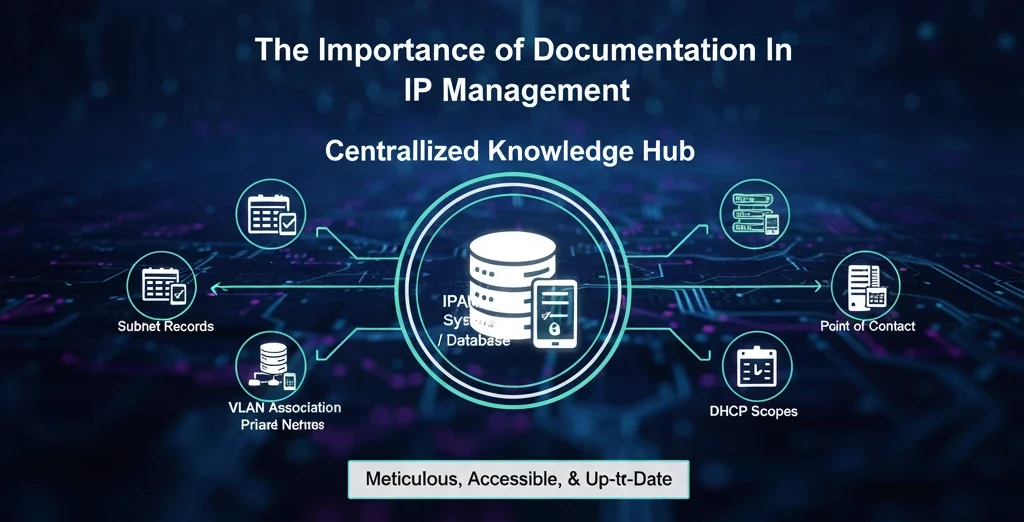
A perfect IP plan is useless if it only exists in one person’s head or in a stale spreadsheet on a forgotten server. Meticulous, accessible, and up-to-date documentation is the glue that holds everything together. The only trustworthy source of knowledge regarding the entirety of your IP address space should be your documentation. This includes an IPAM system or database that maintains records of every subnet, its VLAN association, its DHCP scope, its purpose, and its point of contact, and also detailed network diagrams that graphically depict your subnets and their relationships. The documentation needs to be updated concurrently with each change. Network management becomes transformed from a dark art into a standardized and auditable technique by this discipline.
“The gap between a good network and a great network often comes down to documentation,” notes Jennifer English, a senior analyst at IDC covering enterprise networks. “In times of crisis, when a network is under attack or a critical link has failed, the team does not have time to go on a scavenger hunt for information. Well-maintained IP documentation allows for rapid triage and resolution. It’s a force multiplier for your network operations centre.”
Establishing a robust IP address management policy
Establishing an a thorough IP Address Management (IPAM) policy is a vital—and yet commonly overlooked— component of strategic IP management. This document is your organization’s formal playbook, outlining the standards and procedures that all of your employees—from networking and security to cloud operations and development—must adhere to. Even the most meticulously planned IP plan may rapidly fall aside simply because of ad hoc exceptions, special requests, and a general lack of coordination in the lack of such a governing policy, reintroducing the network to the very state of chaos you attempted to remove. A powerful technical design has been transformed into an operational standard that is both enforceable and permanent from the policy. Clearly establishing roles and duties is the fundamental stage toward establishing an effective IPAM policy.
It ought to indicate who in the business has the right to request a block of IP addresses that remain static or a new subnet. It must additionally state who has the authority to grant these requests, who is in in charge of the technical implementation, as well as—most important of all—who is in in charge of looking after the IPAM system and central documentation. In big businesses, where different parts may have conflicting priorities and have no knowledge of the global network architecture, it is crucial to establish this clear request-and-approval workflow. The process is converted from one of unauthorized requests and tribal knowledge to an uniform, repeatable, and auditable business process by avoiding the uncontrolled proliferation of IP allocations while also making sure that every change is carefully evaluated, supported, and tracked.
The policy have to ask stringent operational standards in along with governance. Strict naming standards have to be obeyed by all network entities in light of this. As opposed to using a mysterious internal code, a subnet should have a name that accurately reflects its location and purpose, such as UK-LON-OFFICE-USER-VLAN110. An engineer are able to rapidly recognize a device from its IP address alone while device hostnames adhere to convention and include location and function codes. The following significantly reduces the mean time to resolution during an outage. Finally, a regular review and reclamation process must be defined in the policy. Projects come to an end, devices is retired, and offices are reduced; networks are natural. These retired assets’ IP addresses need to be meticulously discovered and brought once more to the pool of available addresses.
The looming shadow and bright future of IPv6
Without addressing IPv6, the elephant in the room, no discussion of present-day IP allocation is complete. Organizations are starting to get IPv6 address space from their service providers as an outcome of the concrete reality of IPv4 address exhaustion. It’s a common mistake to make decisions of IPv6 as a separate, future project that can be detached. Planning for IPv6 integration right away as you can is the best option for action. Giving away IPv6 calls for a completely different method of considering. With 340 undecillion addresses, the address space is so broad that conservation is no longer a concern. The entire a focus switches to logical structure and synthesis. Making management and dual-stack operation simple, your IPv6 plan ought to run in parallel with your IPv4 hierarchy, ideally mirroring it.
For the majority of companies, it is recommended to run IPv4 and IPv6 simultaneously (a configuration dubbed dual-stack), to ensure a smooth transition. Developing competence in IPv6 addressing now can assist the way you stay away a hasty, unprepared migration later.
Trusted IPv4 Leasing for Business Growth
Get enterprise-grade IPv4 space quickly, with seamless deployment and end-to-end management.
Get Started with i.leaseFAQs
What is the first step if our current IP allocation is a mess?
The absolute first step is to perform a comprehensive audit using network discovery tools to map out exactly what you have. Include all the networks and network subnets that are at present in use, in addition with their sizes, purposes, and usage rates. What you cannot comprehend, you are unable to fix. Following that, establish a new plan to define the logical hierarchy and start carefully adapting the moving elements of the network to this new scheme, beginning with low-risk areas.
How does good IP allocation improve network security?
A logical and consistent IP scheme allows for the creation of clear and effective security policies. Subnets may be utilized to establish firewall rules, thereby rendering it straightforward to enable or disable traffic from particular places or business units. Furthermore, it makes unusual behavior more apparent; security monitoring systems are going to recognize it right away if a device in the 10.84.0.0/16 range (London) suddenly wants to authenticate from a server subnet in a different country.
What is the difference between public and private IP addressing, and how should we use them?
Public IP addresses are globally routable on the internet and are a finite resource. Only devices that require to be easily accessible from the internet, including your mail servers or public web site, should use them as well. For the purpose to maintain your public IPs and add a layer of anonymity and security through Network Address Translation (NAT), the vast majority of your devices should use private addresses.
When should we consider using an IPAM tool?
An IPAM tool becomes highly recommended if you are in the position to manage more than certain subnets. It offers you an advanced platform for monitoring, distributing, and conserving IP address space, instead of spreadsheets that can be prone to mistakes. For entire lifecycle management of your IP resources, it commonly integrates with DNS and DHCP servers, serves as a centrally located database, and may assist in avoiding disputes.
Why can’t we just put off implementing IPv6?
While NAT and private addressing have delayed the urgency for IPv4, the industry is steadily moving towards IPv6.IPv6 has become native to many new mobile and Internet of Things devices. If you put away planning, you could have to deal with the consequences of rash, expensive, and inadequately carefully planned implementation later. A controlled, strategic dual-stack deployment that was achievable by early planning provides seamless connectivity and secures your network for several decades to come.
Related Blogs
Related Posts

Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises
Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key points Distinguishes between inbound (leasing in) and outbound (leasing out) IPv4 approaches and their strategic implications. Highlights contract structures, registry risk management and continuity considerations affecting global number resources. Inbound vs. outbound IPv4 leasing: complete enterprise guide In the post-exhaustion era of Internet Protocol version 4 (IPv4),Read more Related Posts Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key Read more Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to turn idle IPv4 addresses into a recurring revenue stream with iLease Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

Common Myths About Selling IP Addresses
The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they fear the perceived complexity or legal “gray areas.” As IPv4 exhaustion becomes a permanent reality, the value of these addresses has skyrocketed, yet misconceptions continue to stall potential transactions. At i.lease, powered by the real-world expertise of LARUS, we’ve seen how these myths prevent companies from unlocking significant capital.Read more Related Posts Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key Read more Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to turn idle IPv4 addresses into a recurring revenue stream with iLease Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }

How to buy IPv4 addresses through a certified IP broker
Buying IPv4 space requires policy compliance, verified need, and registry approval, making certified IP brokers essential guides through complex global transfers. IPv4 transactions are regulated transfers, not simple purchases — registries must approve documentation, justification and registration changes. Certified brokers reduce risk and delay by aligning buyers with registry policy, routing legitimacy and cross-region requirements. Why companies still need to buy IPv4 addresses The global supply of IPv4 addressesRead more Related Posts Inbound vs. Outbound IPv4 Leasing: A Complete Guide for Enterprises Understanding IPv4 leasing helps enterprises manage scarce address space, reducing risk and unlocking strategic growth opportunities in today’s digital economy. Key Read more Common Myths About Selling IP Addresses The IPv4 secondary market is often shrouded in mystery, leading many organizations to sit on valuable digital assets because they Read more How to turn idle IPv4 addresses into a recurring revenue stream with iLease Unlock the hidden value of unused IPv4 addresses with iLease, turning dormant digital infrastructure into a recurring revenue stream while Read more .related-post {} .related-post .post-list { text-align: left; } .related-post .post-list .item { margin: 5px; padding: 10px; } .related-post .headline { font-size: 18px !important; color: #999999 !important; } .related-post .post-list .item .post_thumb { max-height: 220px; margin: 10px 0px; padding: 0px; display: block; } .related-post .post-list .item .post_title { font-size: 16px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } .related-post .post-list .item .post_excerpt { font-size: 13px; color: #3f3f3f; margin: 10px 0px; padding: 0px; display: block; text-decoration: none; } @media only screen and (min-width: 1024px) { .related-post .post-list .item { width: 30%; } } @media only screen and (min-width: 768px) and (max-width: 1023px) { .related-post .post-list .item { width: 90%; } } @media only screen and (min-width: 0px) and (max-width: 767px) { .related-post .post-list .item { width: 90%; } }