Blog

Introduction to the Idea of Buying IP Blocks Table of Contents Toggle Introduction to the Idea of Buying IP BlocksExpanding Networks and Infrastructure Supporting Data Centres and Hosting Services Compliance with Regional and Legal Requirements Managing Corporate Mergers and AcquisitionsImproving Network Reputation and Email Deliverability Controlling Costs and Avoiding Dependence on Leases Enabling Cloud and
Go ahead
Categories : Blog, Uncategorized-EN
Posted by Stephanie

Introduction to the Idea of IP Allocation An IP address is what allows your device to join the Internet. It is a number that points to your location in the network. Each time you open a web page or send an email, that number helps data find its way. The
Go ahead

16October
How Subnetting Impacts IP Allocation
Table of Contents Toggle Introduction to Subnetting and IP Allocation What is Subnetting?How Subnetting Impacts IP Allocation Maximising IP Address UsageImproved Network PerformanceEnhanced SecuritySimplified Network ManagementKey Considerations When Subnetting for IP Allocation Common Subnetting MistakesTrusted IPv4 Leasing for Business GrowthFAQsRelated Blogs Subnetting is a key concept in the field of IP network management.
Go ahead
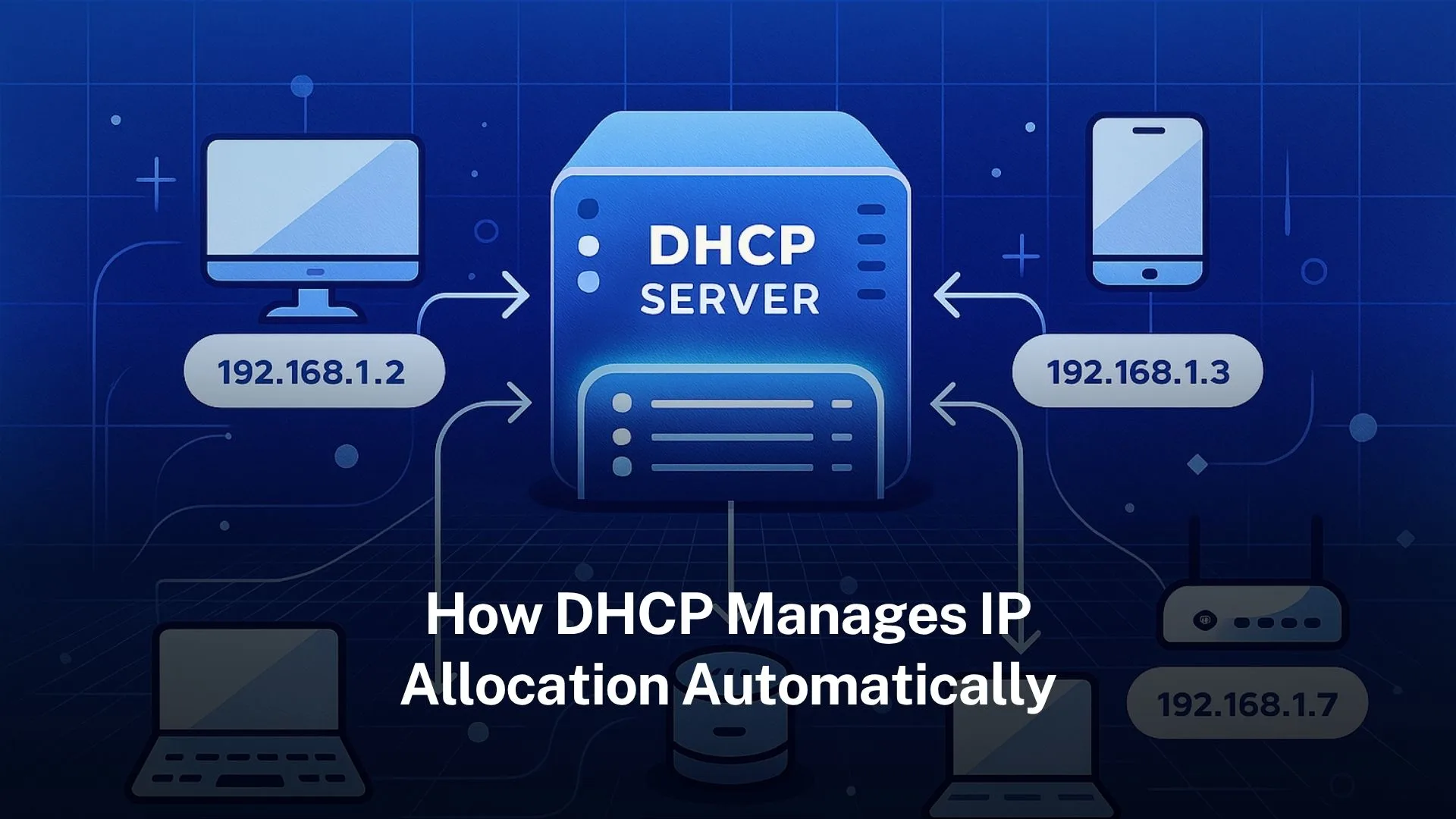
Table of Contents Toggle What is DHCP and why it mattersOrigins and standards behind DHCPCore components of DHCP How DHCP works: the DORA process Lease time, renewal, rebinding: managing durationAdditional network configuration via DHCP optionsPreventing conflicts and ensuring reliability Variations in implementations and policiesCommon challenges in DHCP and how to avoid them Examples of
Go ahead

30September
The Impact of IPv4 Shortage on IP Allocation
The Global IPv4 Shortage and Its Far-Reaching Effects Table of Contents Toggle The Global IPv4 Shortage and Its Far-Reaching EffectsChanging Patterns in IP AllocationTechnical and Operational Responses to ScarcityEconomic and Strategic Implications for the FutureTrusted IPv4 Leasing for Business GrowthFAQsRelated Blogs The Internet uses numbers called Internet Protocol addresses. Each
Go ahead
